TL;DR: You’ll stop hackers from hijacking your Pi in seconds—secure boot for Raspberry Pi with hardware verification prevents the SD card attacks that bypass every other security measure.
Why Should We Care About Secure Boot for Raspberry Pi?
Secure boot for Raspberry Pi is a fundamental yet often overlooked security measure. When developing Pi projects, most enthusiasts and even professional developers focus on functionality first, leaving security as an afterthought. This approach creates significant vulnerabilities, especially as Raspberry Pi boards increasingly power critical applications in industry, healthcare, and smart infrastructure. This article explores why secure boot for Raspberry Pi matters and introduces Zymbit’s Bootware as a straightforward solution that doesn’t require extensive technical expertise or kernel modifications.
This post is sponsored by Zymbit.
Key Takeaways
- Raspberry Pi devices lack built-in secure boot capabilities, making them vulnerable to boot-level attacks
- Physical access to a Pi’s SD card allows attackers to modify boot files, compromise systems, and steal sensitive data
- Implementing secure boot for Raspberry Pi creates a verified chain of trust from hardware to applications
- Traditional secure boot implementation requires significant technical expertise and time investment
- Zymbit’s Bootware offers a simplified secure boot solution with hardware root of trust capabilities
What Is Secure Boot and Why Is It Missing from Raspberry Pi?
Secure boot is a security standard that ensures a device boots using only software trusted by the device manufacturer or system administrator. It creates a chain of trust that begins at the hardware level and extends through each stage of the boot process, verifying the integrity and authenticity of software components before they execute.
Unfortunately, stock Raspberry Pi devices don’t implement secure boot by default. When a Raspberry Pi powers on, it loads boot files directly from the SD card without verifying their authenticity or integrity. This fundamental gap creates a significant security vulnerability that malicious actors can exploit.
Why does this matter? Because without secure boot for Raspberry Pi, anyone with physical access to your Raspberry Pi can modify the boot sequence, inject malicious code, or completely replace your operating system with a compromised version—all without detection.
Can Someone Really Hack My Raspberry Pi Through the Boot Process?
Yes, and it’s alarmingly simple. The Raspberry Pi’s boot vulnerability stems from its unverified boot sequence and easily accessible storage media. Without secure boot protection, attackers can exploit these weaknesses through several attack vectors:
The SD card vulnerability presents the most straightforward attack surface. Anyone with physical access to your Raspberry Pi can remove the SD card, modify its contents on another computer, and reinsert it. This could involve installing rootkits, backdoors, or replacing legitimate software with malicious versions. Since the Pi has no way to verify if the boot files have been tampered with, it will happily execute the compromised code.
Boot chain manipulation is equally concerning. Attackers can modify the bootloader to execute unauthorized code before the operating system loads, potentially compromising the entire system before any security measures activate. This “evil maid” attack (named for scenarios where someone briefly accesses an unattended device, like a hotel maid entering a room) can happen in seconds with the right tools.
When Does Secure Boot Become Essential for Raspberry Pi Projects?

Secure boot for Raspberry Pi transitions from a “nice-to-have” to an essential security measure when your device leaves the controlled environment of your desk. Consider these scenarios where secure boot protection becomes critical:
For commercial products using Raspberry Pi as a foundation, secure boot protects your intellectual property and prevents unauthorized firmware modifications. Without it, competitors could potentially extract your proprietary software or inject malicious code that damages your brand reputation.
In industrial IoT applications, where Raspberry Pis control equipment or gather sensitive data, secure boot for Raspberry Pi ensures device integrity. Manufacturing facilities, energy infrastructure, and smart buildings all require trustworthy device operation that only verified software can provide.
For payment systems or financial applications, secure boot helps meet PCI DSS compliance requirements that specify secure boot as a protection measure. Without it, payment data could be compromised through boot-level attacks that bypass application security measures.
The consequences of bootloader-level compromises can be severe and far-reaching. Unlike application-level vulnerabilities that might be contained by the operating system, boot-level compromises can completely circumvent all security measures implemented at higher levels. This makes secure boot a foundational element for any serious security strategy.
Why is Secure Boot So Difficult to Implement on Raspberry Pi?

Implementing secure boot for Raspberry Pi has traditionally been a complex, time-consuming process that requires specialized knowledge. This complexity has led many developers to skip secure boot implementation entirely, leaving their devices vulnerable.
The technical barriers are substantial. Traditional secure boot implementation requires custom firmware development, kernel modifications, and cryptographic key management systems. Each of these components demands specialized knowledge in low-level system programming, cryptography, and hardware security—expertise that many Raspberry Pi developers simply don’t possess.
The time investment required is equally prohibitive. A proper DIY secure boot implementation can take weeks or months to develop, test, and refine. For teams working under tight deadlines or individual developers with limited resources, this time commitment often seems impossible to justify—especially when the device “works fine” without it.
Documentation and support for custom secure boot implementations are also fragmented and often outdated. Developers must piece together information from various sources, experiment with undocumented features, and sometimes reverse-engineer components to achieve their security goals.
These barriers collectively create what security experts call the “security implementation gap”—the difference between known best practices and what actually gets implemented in real-world projects. For Raspberry Pi development, this gap is particularly wide when it comes to secure boot.
What Components Make Up a Proper Secure Boot Implementation?
A robust secure boot implementation consists of several critical components working together to create an unbroken chain of trust from hardware to applications.
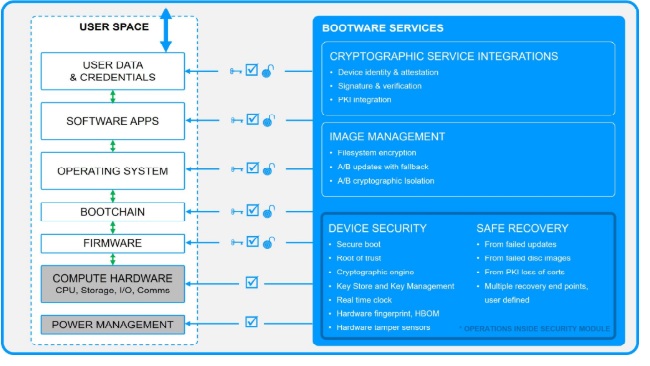
The hardware root of trust serves as the foundation for secure boot. This tamper-resistant hardware element contains cryptographic keys and verification mechanisms that cannot be altered by software attacks. In secure systems, this root of trust verifies the first stage of the boot process, establishing the initial link in the chain of trust. The root of trust typically includes capabilities for storing encryption keys, performing cryptographic operations, and detecting physical tampering attempts.
Bootloader verification ensures that only authorized bootloaders can execute. The bootloader is particularly critical since it’s the first software that runs and has privileged access to the system. A compromised bootloader can completely undermine all other security measures. In a secure boot implementation, the bootloader’s integrity and authenticity are verified using cryptographic signatures stored in or verified by the hardware root of trust.
Kernel and filesystem verification extends the chain of trust to the operating system itself. After the bootloader has been verified, it then verifies the kernel before transferring control. Similarly, the verified kernel can ensure it only loads verified system components. This process continues through each stage of system initialization, creating an unbroken chain of verified software components.
Signature verification using public key cryptography is the mechanism that makes these verifications possible. Each component in the boot chain is cryptographically signed by a trusted authority (usually the device manufacturer or system administrator). Before a component executes, its signature is verified against trusted public keys stored in protected storage.
Effective key management forms the backbone of secure boot systems but is often overlooked. This includes secure generation of signing keys, safe storage of private keys, distribution of public verification keys, and processes for key rotation or revocation if compromised. Many DIY secure boot implementations falter at this stage—developers might implement verification correctly but store their signing keys insecurely or fail to plan for key lifecycle management, creating significant vulnerabilities.
Introducing Bootware: How Zymbit Simplifies Secure Boot for Raspberry Pi
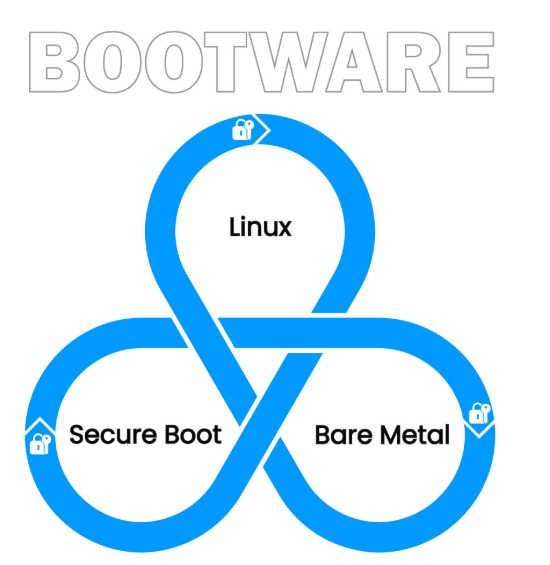
Zymbit’s Bootware offers a radically simplified approach to implementing secure boot for Raspberry Pi systems by unifying three critical elements: Linux, Secure Boot, and Bare Metal. This integrated solution manages the complex interactions between your operating system (Linux), verification process (Secure Boot), and hardware foundation (Bare Metal)—eliminating the technical barriers that prevent many developers from implementing proper security.
Rather than requiring expertise in all three domains, Bootware automatically manages these intersections, delivering enterprise-grade protection while preserving your familiar development environment. This unified approach addresses the security implementation gap that leaves many Raspberry Pi projects vulnerable to boot-level attacks.
Unlike DIY approaches that require extensive modifications to the Raspberry Pi’s boot process, Bootware integrates with standard Raspberry Pi OS (formerly Raspbian) and Ubuntu distributions. This compatibility means you can implement secure boot without abandoning familiar development environments or operating systems. Bootware works alongside your existing software stack rather than requiring a complete overhaul.
The hardware foundation for Bootware’s security comes from Zymbit’s hardware security modules (such as ZYMKEY4) that attach directly to the Raspberry Pi’s GPIO pins. These modules provide the critical hardware root of trust that’s missing from stock Raspberry Pi boards. They store cryptographic keys in tamper-resistant silicon and perform verification operations independently from the main processor, creating a true hardware-based security boundary.
Bootware’s approach is comprehensive, addressing not just boot verification but the entire secure device lifecycle. It includes support for encrypted filesystems, secure update mechanisms, and recovery options if verification fails. This holistic approach ensures that boot security integrates seamlessly with other security measures rather than existing as an isolated protection mechanism.
Implementation simplicity is perhaps Bootware’s most significant advantage. What would typically require weeks of custom development can be implemented in hours, with clear documentation and proven components. This dramatically lowers the expertise barrier, making secure boot accessible to developers without specialized security backgrounds.
How Does Bootware Create a Secure Boot Process?
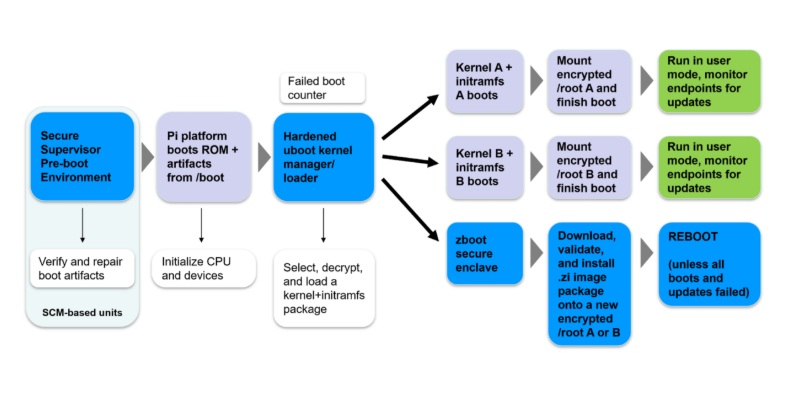
Bootware implements secure boot for Raspberry Pi through a carefully designed architecture that balances security with usability. At its core, Bootware creates a verified boot path that ensures only authorized software runs on your Raspberry Pi.
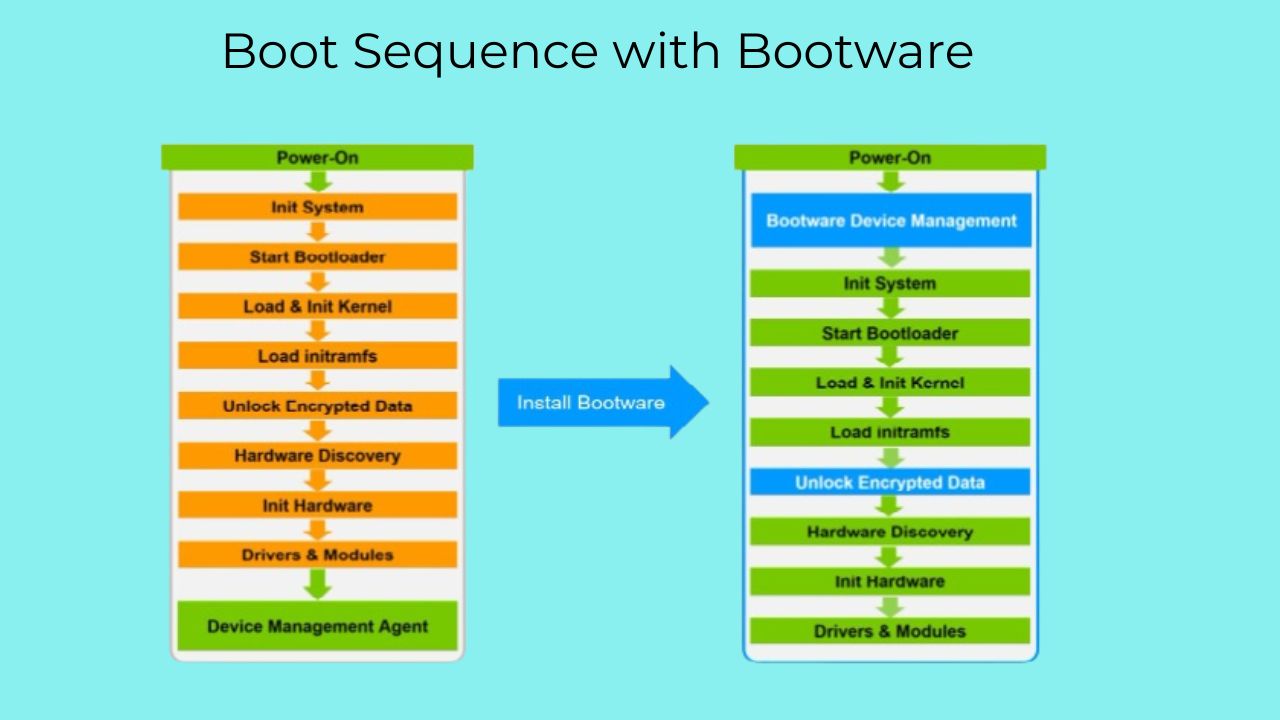
The A/B partition system is a key component of Bootware’s design. Your Raspberry Pi’s storage is divided into two complete system images (A and B), with only one active at a time. This approach allows for secure updates—a new system image can be written to the inactive partition, verified for authenticity, and then made active only if verification succeeds. If something goes wrong during an update or boot attempt, the system can automatically fall back to the previously working partition.
Hardware-based verification provides the security foundation. When paired with a Zymbit hardware security module like Zymkey, Bootware leverages tamper-resistant hardware to store cryptographic keys and perform verification operations. This creates a hardware root of trust that software-only solutions cannot match. The hardware module verifies the bootloader’s integrity, which then verifies the kernel, creating an unbroken chain of trust from hardware to applications.
Bootware’s recovery mechanisms ensure system reliability even when verification fails. If both the A and B system partitions fail verification (which might happen if both were tampered with), Bootware can fall back to a minimal recovery system that allows for administrator intervention. This ensures that even sophisticated attacks cannot permanently brick your device.
The verification process itself uses industry-standard cryptographic techniques. System components are signed with private keys held by the device administrator, while corresponding public keys stored in the hardware security module verify these signatures during boot. This asymmetric cryptography ensures that even if an attacker can read the verification keys, they cannot create valid signatures for modified software.
How Difficult Is It to Add Secure Boot to My Raspberry Pi Project?
Implementing secure boot for Raspberry Pi with Zymbit’s Bootware is remarkably straightforward compared to traditional methods. The process focuses on integration rather than custom development, making it accessible to most developers regardless of security expertise.
To get started with Bootware, you’ll need a compatible Raspberry Pi (most models including Pi 3, 4, and CM4 are supported), a Zymbit security module like Zymkey4 or Zymkey Zero for the hardware root of trust, and a standard Raspberry Pi OS or Ubuntu installation. The hardware integration is plug-and-play—the Zymkey module attaches directly to the Raspberry Pi’s GPIO pins without requiring soldering or complex wiring.
The software installation process is guided by clear documentation. After installing the Zymbit software packages, a setup utility walks you through the configuration process, including generating or importing cryptographic keys, setting up the A/B partition scheme, and defining security policies. This guided approach eliminates much of the guesswork that makes traditional secure boot implementation challenging.
Time investment is minimal compared to DIY approaches. While a custom secure boot implementation might take weeks or months, setting up Bootware typically requires only a few hours for basic configurations. Even complex deployments with custom security policies can usually be completed in days rather than weeks. This efficiency makes secure boot for Raspberry Pi a practical addition to projects with tight timelines.
Integration with existing projects is designed to be non-disruptive. If you have an existing Raspberry Pi application, Bootware can be added without requiring significant changes to your application code. Your software continues to run normally, with security enforced at the boot level rather than requiring application-level modifications.
How Does Secure Boot Fit into a Broader Security Approach?
While secure boot provides critical protection for your Raspberry Pi, it works best as part of a comprehensive security strategy. Understanding how boot security complements other measures helps create truly resilient systems.
Encrypted filesystems work hand-in-hand with secure boot to provide data protection. Secure boot for Raspberry Pi ensures only authorized code runs on your device, while encryption ensures that stored data remains protected even if physical access to the storage media is obtained. Zymbit’s Bootware supports integration with Linux’s dm-crypt/LUKS encryption, with encryption keys stored in the tamper-resistant hardware security module rather than on the vulnerable SD card.
Tamper detection extends protection to the physical realm. Since physical access to devices represents a significant threat vector, detecting and responding to tamper attempts is crucial. Zymbit’s hardware modules include accelerometers and other sensors that can detect physical interference, triggering protective responses like key erasure or system shutdown.
Secure update mechanisms ensure that your security remains effective over time. As vulnerabilities are discovered and patched, your devices need secure ways to receive updates without creating new attack vectors. Bootware’s A/B partition scheme with cryptographic verification ensures that only authentic updates from authorized sources can be installed.
Ongoing security maintenance requires planning and infrastructure. Regular firmware updates, key rotation schedules, and security monitoring should all be part of your long-term strategy. The best security implementations include not just technical measures but also processes and policies that support them throughout the device lifecycle.
How Does Secure Boot Transform Real Projects?
Let’s look at a hypothetical scenario. A small industrial automation company provides a compelling example of how implementing secure boot transformed their Raspberry Pi-based product security. Their journey illustrates the challenges and benefits of prioritizing boot security.
The company initially developed a prototype industrial controller using Raspberry Pi Compute Module 4, focusing primarily on functionality. Their device controlled sensitive manufacturing equipment and collected valuable production data. During pre-production security assessment, they identified several critical vulnerabilities stemming from the unsecured boot process. A penetration testing team demonstrated how easily an attacker could modify the boot files to gain complete control of the system.
Implementing traditional secure boot seemed daunting given their compressed development timeline and limited security expertise. The team estimated that a custom secure boot implementation would require at least two months of development time and specialized knowledge they didn’t possess.
After discovering Zymbit’s Bootware solution, they integrated a Zymkey hardware security module and implemented the secure boot process in less than a week. The implementation protected the boot chain from unauthorized modifications and added encrypted storage for sensitive configuration and production data.
The security improvements didn’t compromise system performance or reliability. In fact, the A/B partition scheme improved the update process reliability, reducing downtime during software updates. The hardware-based security also became a marketable feature that differentiated their product from competitors.
The most valuable lesson from their experience was the importance of addressing security fundamentals early in the development process. While they successfully implemented secure boot for Raspberry Pi before production, integrating it during the initial design phase would have saved considerable rework and development time.
Frequently Asked Questions
Can Raspberry Pi be easily hacked if secure boot isn’t implemented?
Yes, without secure boot, anyone with physical access to your Raspberry Pi can remove the SD card, modify the boot files to include malicious code, and reinsert it. The Pi will boot the compromised system without any verification, potentially giving attackers complete control over your device.
Does secure boot slow down the Raspberry Pi boot process?
Secure boot adds minimal overhead to the boot process. While there is a slight increase in boot time due to signature verification (typically 1-3 seconds), this minor delay provides crucial security benefits that far outweigh the performance impact.
Can I implement secure boot on Raspberry Pi without additional hardware?
True secure boot requires a hardware root of trust that’s separate from the main processor. While software-only approaches exist, they can’t provide the same level of protection since they lack the isolated, tamper-resistant environment needed to store keys and perform verification securely.
Is secure boot necessary for home projects or just commercial products?
While commercial products have more obvious security requirements, even home projects benefit from secure boot if they control important systems (home automation, security cameras) or handle sensitive data. As smart home devices increasingly control physical aspects of our homes, proper security becomes important even for personal projects.
How does secure boot differ from disk encryption on Raspberry Pi?
Secure boot and disk encryption address different security concerns. Secure boot prevents unauthorized code execution by verifying software integrity before it runs. Disk encryption protects data confidentiality by making stored information unreadable without the correct key. Together, they provide comprehensive protection against both code tampering and data theft.
Will secure boot prevent all types of attacks on my Raspberry Pi?
No, secure boot specifically protects against boot-level attacks that modify system software. While it’s a crucial security layer, a comprehensive approach should also include network security, application security, physical security measures, and regular software updates to address known vulnerabilities.
Conclusion: Security Doesn’t Have to Be a Technical Hurdle with Bootware
Secure boot for Raspberry Pi is no longer an optional luxury —it’s a necessity for any device that handles sensitive data, controls important systems, or operates outside controlled environments. The risks of boot-level compromises are too significant to ignore, yet traditional implementation challenges have prevented widespread adoption of this critical security measure.
Zymbit’s Bootware approach demonstrates that security and simplicity aren’t mutually exclusive. By combining plug-and-play hardware security modules with intelligent software design, secure boot becomes accessible to developers without specialized security expertise. This democratization of security technology helps close the gap between security best practices and real-world implementation.
As you develop your next Raspberry Pi project, consider security requirements from the beginning rather than as an afterthought. Implementing secure boot for Raspberry Pi early in the development process is significantly easier than retrofitting security onto an existing design. With solutions like Bootware available, there’s no longer a valid reason to leave your devices vulnerable to boot-level attacks.
Take the next step in securing your Raspberry Pi projects by exploring hardware-based security solutions like Zymbit that provide protection without overwhelming complexity. Your users, customers, and future self will thank you for building security into the foundation of your systems.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.

