TL;DR: You’ll transform your vulnerable $35 Pi into an enterprise-grade fortress with hardware-based encryption and tamper detection that prevents million-dollar security breaches.
Why Consider Hardening Your Raspberry Pi?
The Raspberry Pi has revolutionized computing for hobbyists and professionals alike, but the journey from weekend project to enterprise-grade deployment requires serious security considerations. Hardening your Raspberry Pi transforms it from a vulnerable prototype into a robust, tamper-resistant system capable of withstanding real-world threats. This guide explores the essential steps in implementing production-grade security measures using Zymbit’s hardware security modules and Bootware software, bridging the gap between maker projects and mission-critical deployments.
This post is sponsored by Zymbit.
Key Takeaways
- Unprotected Raspberry Pi devices have critical security vulnerabilities that make them unsuitable for production environments
- Hardware-based security is essential for protecting keys, credentials, and sensitive data on edge devices
- Implementing secure boot, encrypted storage, and tamper detection transforms your Pi into a mission-critical solution
- Zymbit’s HSM modules provide plug-and-play security with minimal integration effort
- A proper security implementation protects both intellectual property and operational integrity
The Security Gap: Why Your Raspberry Pi Isn’t Ready for Production
When your weekend project moves from your workbench to the field, security vulnerabilities suddenly become serious business risks. Out-of-the-box Raspberry Pi boards lack fundamental security protections required in production environments. The SD card—the heart of your Pi’s storage system—can be easily removed, cloned, or replaced by anyone with physical access to the device. Without encryption, all your code, credentials, and data are exposed in plain text.
The Raspberry Pi’s boot process presents another critical vulnerability. With no secure boot capability, there’s nothing to verify the authenticity of the operating system or application code during startup. An attacker can modify the boot partition or replace system files, potentially gaining complete control over your device. Even more concerning, there’s no hardware root of trust—the foundation of a secure computing system that verifies the integrity of every software component from boot to application.
These gaps create an unacceptable risk for business applications. A device that was perfectly adequate for prototyping becomes a liability when deployed in unattended locations, processing sensitive data, or controlling critical infrastructure. The question isn’t whether your unprotected Raspberry Pi can be compromised—it’s how quickly and with what consequences.
The True Cost of a Security Breach: Beyond the Technical Impact

When considering the security of your Raspberry Pi deployments, it’s essential to understand what’s truly at stake. The financial implications of a security breach extend far beyond the $35-55 cost of the board itself. Your SD card might cost $5, but what about the intellectual property stored on it? Custom software, algorithms, machine learning models, and proprietary configuration data can represent millions in research and development investment.
Security breaches carry regulatory and compliance implications as well. Depending on your industry, compromised devices could lead to violations of GDPR, HIPAA, or other regulatory requirements, resulting in significant fines and legal expenses. For publicly traded companies, security incidents can impact stock prices and investor confidence. The Ponemon Institute reports that the average cost of a data breach now exceeds $4.45 million globally, with costs continuing to rise year over year.
Perhaps most concerning for industrial applications are the operational risks. A compromised Raspberry Pi controlling industrial equipment, infrastructure, or safety systems could cause physical damage, service interruptions, or even endanger human safety. These impacts can far outweigh the direct financial costs of the breach itself, making proper security an essential investment rather than an optional expense.
The Five Critical Security Requirements for Hardened Your Raspberry Pi
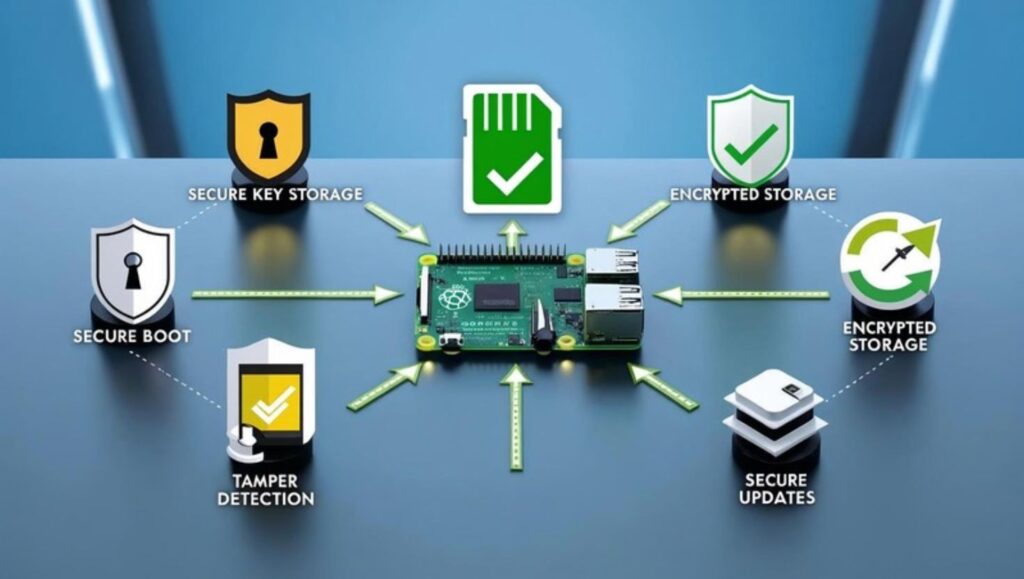
When hardening your Raspberry Pi from a development platform into a production-ready device, you need to implement five essential security features. These components work together to create a comprehensive security architecture capable of protecting against both physical and digital threats.
First, hardware-based secure key storage forms the foundation of your security strategy. Cryptographic keys must never be stored in regular memory or on the SD card where they can be extracted. A hardware security module (HSM) provides a dedicated, tamper-resistant environment for key generation, storage, and cryptographic operations. This ensures that even if an attacker gains access to your device, the critical keys remain protected.
Second, encrypted storage protects data at rest. When properly implemented with a hardware root of trust, full disk encryption ensures that information stored on the SD card remains secure even if the card is physically removed from the device. This protects both intellectual property (your code) and operational data. The encryption keys should be stored in the hardware security module, creating a secure dependency that prevents decryption on unauthorized hardware.
Third, secure boot verifies the integrity and authenticity of your system from the moment it powers on. Each component in the boot chain—from bootloader to kernel to applications—is cryptographically verified before execution. This prevents attackers from inserting malicious code or modified components into your system. When combined with A/B partitioning, secure boot also enables safe, reliable updates with fallback options.
Fourth, physical tamper detection provides an essential layer of protection for devices in unattended locations. Sensors that detect chassis intrusion, movement, or environmental changes can trigger appropriate responses—from logging the event to completely wiping sensitive keys. This creates a security perimeter that extends beyond the digital realm into the physical world.
Finally, secure update mechanisms ensure your device can receive patches and improvements without creating new vulnerabilities. Updates should be cryptographically signed, verified before installation, and deployed in a way that prevents partial or corrupted updates from bricking your device. This maintains the security and reliability of your system throughout its operational life.
Meet the Zymbit Security Solution: How Does Hardware-Based Security Work?
Hardening your Raspberry Pi requires more than software-based protections—you need a dedicated hardware security foundation. Zymbit offers an integrated solution that combines purpose-built hardware security modules with specialized software to transform your Raspberry Pi into a truly production-ready device.
At the core of Zymbit’s approach is the concept of layered security. The HSM4 and HSM6 modules connect directly to your Raspberry Pi’s GPIO header, providing a hardware root of trust separate from the main processor. This creates a security boundary that protects keys and sensitive operations even if the main system is compromised. These modules include secure elements for cryptographic operations, battery-backed tamper detection sensors, and real-time clocks that maintain accurate time even when main power is lost.
What makes Zymbit’s approach particularly valuable for makers transitioning to production is its accessibility. Unlike complex enterprise security solutions that require specialized expertise, Zymbit’s modules are designed for plug-and-play integration. Installation takes minutes, with straightforward software setup and comprehensive documentation. This democratizes hardware security, making it accessible to small teams and individual developers while still providing enterprise-grade protection.
Hardware Security Modules: How Do HSM4 and HSM6 Protect Your Raspberry Pi?

Zymbit’s hardware security modules represent the physical foundation of a comprehensive security strategy for Raspberry Pi deployments. The HSM4 and HSM6 modules are purpose-built security devices that provide hardware-anchored protection for keys, credentials, and cryptographic operations.
The HSM4 is Zymbit’s standard security module, offering comprehensive protection for most Raspberry Pi applications. It features a secure element that generates and stores cryptographic keys in tamper-resistant silicon, ensuring they never leave the protected boundary. The module includes acceleration sensors that detect physical tampering attempts, two independent perimeter detection circuits for monitoring enclosure integrity, and a battery-backed real-time clock that maintains accurate time even during power loss. This combination creates a security perimeter that extends beyond the digital realm into the physical world.
The HSM6, by contrast, is designed for more advanced cryptographic applications, particularly in blockchain and cryptocurrency environments. It dramatically expands key storage capacity to 512 private/public key pairs and adds support for 128 foreign public keys. The HSM6 functions as an embedded hardware wallet with support for BIP (Bitcoin Improvement Proposal) standards, making it specifically suited for blockchain edge devices, embedded hardware wallets, and on-premise key management applications
While both the HSM4 and HSM6 share the same physical form factor and are designed to enhance security for Raspberry Pi and embedded Linux devices, they differ significantly in their cryptographic capabilities. The HSM4 focuses on essential security features, providing secure key storage, tamper detection, and cryptographic operations for standard IoT security applications. However, it’s limited to storing only 3 private/public key pairs.
While these hardware security modules provide the foundation for hardening your Raspberry Pi, Zymbit’s Bootware software creates a comprehensive security framework that protects your system from boot to operation. Bootware isn’t just an application—it’s an integrated security management system that works in concert with the hardware security modules to provide end-to-end protection.
What is Bootware and How Does It Secure Your System?

Bootware implements a secure boot chain that verifies the integrity and authenticity of every component in your system. This starts with the bootloader and extends through the kernel, root filesystem, and applications.
Each component is cryptographically verified before execution, preventing the insertion of malicious code or unauthorized modifications. This creates a chain of trust anchored in the hardware security module, ensuring that only legitimate software runs on your device.
One of Bootware’s most powerful features is its A/B update system with cryptographic isolation. This creates two complete system partitions, allowing for fail-safe updates even in remote or unattended locations. When an update is received, it’s installed to the inactive partition while the system continues to run from the active one.
Once the update is verified, the system switches partitions on the next boot. If anything goes wrong during the update or the new software fails to boot properly, the system automatically reverts to the previous, known-good configuration. This eliminates the risk of “bricking” devices in the field while maintaining strong security boundaries.
Real-World Applications: Where Are Hardened Raspberry Pi Systems Making an Impact?

Hardened Raspberry Pi systems are finding their way into an increasingly diverse range of mission-critical applications, proving that with proper security measures, these affordable computers can serve as the foundation for enterprise-grade solutions. In industrial automation, secured Raspberry Pi devices are being deployed as edge controllers and data gateways, collecting sensitive production data and interfacing with operational technology networks while maintaining robust security boundaries.
The retail sector has embraced hardened Raspberry Pi systems for point-of-sale terminals, digital signage, and inventory management solutions. In these environments, devices often handle payment information and must comply with PCI-DSS requirements—making hardware security modules essential components. The combination of affordability and robust security makes these systems particularly attractive for businesses deploying large numbers of devices across multiple locations.
Perhaps most impressively, hardened Raspberry Pi systems are finding applications in critical infrastructure. From smart city initiatives to utility monitoring stations, these devices provide cost-effective computing at the edge while maintaining the security posture required for systems that impact public safety and essential services. The ability to detect tampering, encrypt sensitive data, and ensure software integrity has transformed the humble Raspberry Pi from a hobbyist platform into a serious contender for security-conscious deployments.
Frequently Asked Questions
Can a Raspberry Pi be hacked easily?
Yes, an unprotected Raspberry Pi can be relatively easy to hack, especially through physical access. The SD card can be removed and its contents read or modified, default credentials often remain unchanged, and many deployments lack encryption or secure boot capabilities. Implementing hardware security modules, encrypted storage, and tamper detection significantly increases the difficulty of successful attacks.
Is Raspberry Pi secure enough for industrial applications?
Out-of-the-box Raspberry Pi boards lack the security features required for industrial applications. However, when properly hardened with hardware security modules like Zymbit’s HSM4 or HSM6, encrypted storage, secure boot, and tamper detection, Raspberry Pi devices can meet the security requirements for many industrial deployments. The key is implementing appropriate security controls based on your specific threat model.
How much does it cost to secure a Raspberry Pi for production?
Implementing production-grade security for a Raspberry Pi typically adds $40-125 to the base hardware cost, depending on the level of security required. The Zymbit HSM4 module costs approximately $45, while the more advanced HSM6 is around $125. This investment protects both the device itself and the often much more valuable intellectual property and operational data it contains.
What happens if someone steals my secured Raspberry Pi?
A properly secured Raspberry Pi with Zymbit hardware security will detect the theft through tamper sensors and can be configured to automatically erase encryption keys, rendering the data inaccessible. The encrypted storage prevents access to sensitive information even if the SD card is removed, and the hardware binding between the security module and your specific Pi prevents the use of cloned cards or replacement hardware.
Can I still update my Raspberry Pi remotely after implementing security?
Yes, secure remote updates are a key benefit of proper security implementation. Zymbit’s Bootware provides an A/B partition system that allows safe remote updates with automatic rollback if problems occur. Updates are cryptographically verified before installation, ensuring only authentic software is deployed to your device while maintaining continuous operation and automatic recovery from failed updates.
How difficult is it to implement hardware security on Raspberry Pi?
Implementing hardware security with Zymbit modules is designed to be straightforward even for those without specialized security expertise. Physical installation takes just minutes, connecting the module to the GPIO pins. Software installation utilizes a simple script that configures all necessary components. Basic security functions are available through an intuitive API, while advanced features allow customization for specific requirements.
Bridging the Gap: From Maker Project to Production Solution
The journey from a weekend maker project to a production-ready solution no longer requires abandoning the Raspberry Pi platform that made your prototype possible. By implementing proper security measures with Zymbit’s hardware and software stack, you can maintain the advantages of the Pi ecosystem—affordability, flexibility, and community support—while adding the security features necessary for mission-critical deployments.
This security transformation doesn’t just protect your device; it fundamentally changes what’s possible with Raspberry Pi-based systems. Applications that would have previously been considered too sensitive or critical for a hobbyist platform become viable when proper security controls are in place. The familiar development environment that accelerated your prototype can now carry forward into production, reducing development time and preserving your team’s existing expertise.
Ultimately, hardening your Raspberry Pi with Zymbit creates a bridge between the maker and enterprise worlds, combining the best aspects of both. The accessibility and innovation that characterize the maker community can now extend into production environments, protected by security measures that satisfy even the most stringent requirements. This convergence opens new possibilities for startups, small businesses, and enterprise innovation teams looking to bring their ideas to market quickly without compromising on security.
Ready to transform your Raspberry Pi from prototype to production? Visit Zymbit’s website to explore the full range of security solutions, access detailed documentation, and order your developer kit. The Zymbit community forum also provides valuable resources and support from both the Zymbit team and experienced users, helping you navigate the implementation process and optimize your security configuration.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.

