Why Worry About Physical Security for Raspberry Pi?
During the process of Raspberry Pi development, we often focus on software security—firewalls, updates, and access controls. But there’s a glaring blind spot many developers overlook: physical security. When your Pi-powered device sits unattended in the field, what’s stopping someone from simply removing the SD card, extracting your secrets, or modifying your firmware? This physical vulnerability creates a critical security gap that software alone can’t fix. While Raspberry Pi boards have revolutionized prototyping and deployment, they were never designed with tamper-resistance in mind—leaving your intellectual property, credentials, and sensitive data exposed to physical attacks.
As IoT deployments grow, the stakes get higher. Organizations deploying Raspberry Pi devices in industrial, retail, or infrastructure applications face serious consequences if physical security is compromised. This article explores why physical security for Raspberry Pi projects matters and how hardware-based protections like ZYMKEY4 provide a comprehensive defense against tampering.
Imagine a bad actor is passing through your facility and they see a standard Raspberry Pi sitting in a room. Maybe it’s just on a table, but hopefully it’s mounted somewhere out of reach. He comes back a few days later, and when no one is looking either:
- walks out with it to analyze it at their leisure
- Pops the SD card out and takes it with them (who’s gonna see?)
- opens the case and slips in his own hardware to monitor processing
Sounds like science fiction? But any of these are easy to do.
This post is sponsored by Zymbit.
Key Takeaways
- Software-only security fails to protect against physical access to your Raspberry Pi
- SD cards can be easily removed, cloned, or modified without detection
- Hardware Security Modules provide tamper detection that responds to physical attacks
- Implementing physical security is essential when moving from prototypes to production
- Tamper-resistant modules like ZYMKEY4 integrate with existing Pi designs with minimal effort
The Physical Vulnerability of Raspberry Pi Devices

The Raspberry Pi’s open design makes it perfect for learning and prototyping, but problematic for security. Unlike enterprise-grade hardware, standard Raspberry Pi boards lack tamper-resistant features. The SD card is easily accessible and removable—anyone with physical access can extract it, copy its contents, modify the data, and reinsert it without leaving evidence.
This fundamental vulnerability enables several attack vectors. An attacker with even brief physical access can clone your entire system, extract encryption keys stored in files, or install backdoors. Even worse, these attacks often leave no trace, meaning you might never know your system was compromised.
Common Physical Attack Vectors
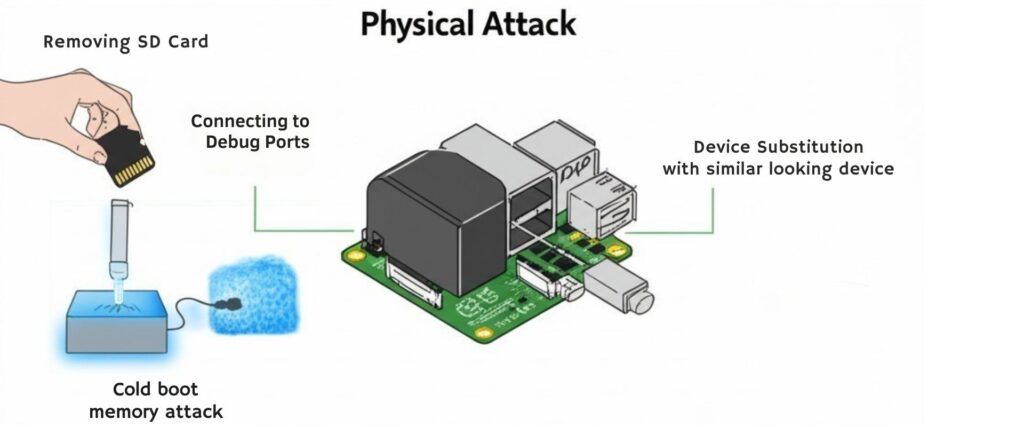
Physical attacks on Raspberry Pi devices come in several forms, each exploiting the hardware’s inherent accessibility:
- SD Card Extraction: The most straightforward attack simply involves removing the SD card, analyzing or copying its contents, and returning it—often undetected.
- Port Access: Exposed UART, GPIO, and USB ports provide direct interfaces to the system, potentially allowing attackers to inject commands or extract data.
- Cold Boot Attacks: Though more sophisticated, these attacks can capture encryption keys by accessing memory contents when power is removed or applied.
- Device Substitution: An attacker might replace your legitimate device with a compromised one that looks identical but contains malicious code.
Beyond these common methods, specialized techniques like voltage glitching or electromagnetic analysis can extract secrets from unprotected devices. We’ll explore these advanced techniques in a future article on “Advanced Physical Attack Methods for Embedded Devices.”
Real-World Consequences of Physical Tampering

When physical security is breached, the impacts extend far beyond the device itself:
- Intellectual Property Theft: Your proprietary algorithms, design secrets, and business logic can be extracted and stolen—potentially devastating for tech startups or R&D projects.
- Credential Compromise: Authentication keys, certificates, and API tokens stored on the device become accessible, potentially compromising cloud systems or backend infrastructure.
- Data Breaches: Customer information, transaction records, or other sensitive data can be extracted, leading to privacy violations and regulatory penalties.
In one real case, a company deploying Raspberry Pi-based payment terminals discovered several devices had been temporarily removed, cloned, and returned with skimming software. Without tamper detection, they only discovered the breach after customer data was already compromised.
The Limitations of Software-Only Security
Many developers rely solely on software-based security measures like encryption, access controls, and secure communications. While these are necessary components of a security strategy, they have fundamental limitations against physical attacks:
- Encryption Keys at Risk: Software encryption depends on keys stored somewhere on the device—keys that can be extracted if an attacker has physical access.
- No Boot Protection: Without hardware-based secure boot, an attacker can modify the boot sequence to bypass security controls or load compromised firmware.
- Undetected Tampering: Software alone can’t detect if someone has physically opened a device, removed components, or cloned storage.
A recent study published in ScienceDirect highlights the severe security vulnerabilities of unprotected Raspberry Pi devices. Researchers conducted penetration testing on Raspberry Pi using three different attack vectors—Man in the Middle, Backdoor, and Denial of Service—comparing them to attacks on Windows systems.
These findings are alarming: attackers were able to breach Raspberry Pi devices running Raspbian significantly faster than Windows 10 systems, with some attacks executing in just one second. The research confirmed that standard Raspberry Pi configurations lack built-in mechanisms to detect intrusions, malicious files, or tampering attempts, making them particularly vulnerable in field deployments. Without hardware-based security measures, these devices remain essentially defenseless against both remote and physical attacks, emphasizing the critical need for dedicated security modules like ZYMKEY4 that provide tamper detection and response capabilities.
This study reinforces what we’ve discussed throughout this article: software-only security measures are inadequate for protecting Raspberry Pi devices deployed in untrusted environments. Physical security must be addressed as a foundational component of any production-grade implementation.
In the end, software security measures assume the hardware remains trustworthy—an assumption that fails when physical access is obtained.
Understanding Tamper Detection and Response
Tamper detection forms a critical component of physical security for sensitive devices. Unlike software protections, hardware-based tamper detection physically monitors for unauthorized access attempts and responds appropriately.
Effective tamper detection systems include:
- Sensors: Physical mechanisms that detect chassis intrusion, movement, temperature changes, or power anomalies that might indicate tampering.
- Response Mechanisms: Systems that take action when tampering is detected, such as erasing encryption keys, shutting down the device, or alerting administrators.
- Persistent Monitoring: Battery-backed circuits that maintain tamper detection even when the device is powered off.
For Raspberry Pi devices deployed in the field, tamper detection provides an essential layer of defense against physical attacks. When someone attempts to open an enclosure or remove a board, the system can immediately respond—protecting your secrets even if the device falls into the wrong hands.
Introducing Hardware Security Modules for Raspberry Pi
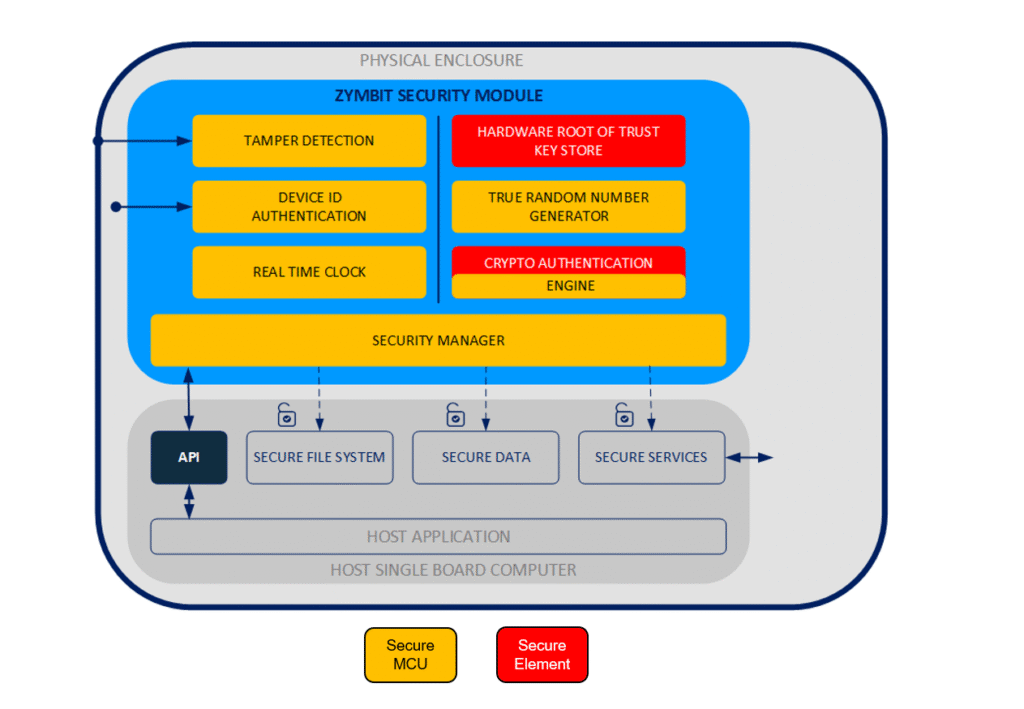
Hardware Security Modules (HSMs) provide purpose-built protection against both digital and physical threats. Unlike software solutions, HSMs implement security in dedicated hardware that’s specifically designed to resist tampering.
For Raspberry Pi, HSMs like ZYMKEY4 offer several advantages:
- Secure Key Storage: Cryptographic keys are generated and stored inside tamper-resistant hardware — never exposed to the main processor or memory.
- Device ID Authentication: Verify the hardware fingerprint of the device on boot, so that nothing has been added or changed.
- Hardware-Based Encryption: Cryptographic operations happen within the secure element, preventing key exposure even when performing encryption or decryption.
- Tamper Detection Circuits: Physical sensors detect and respond to intrusion attempts, movement, or environmental anomalies.
- Device Binding: The HSM creates a unique identity tied to the specific hardware, preventing cloning or replacement attacks.
These physical security features complement software protection to create a comprehensive security architecture.
How ZYMKEY4 Solves Physical Security Challenges
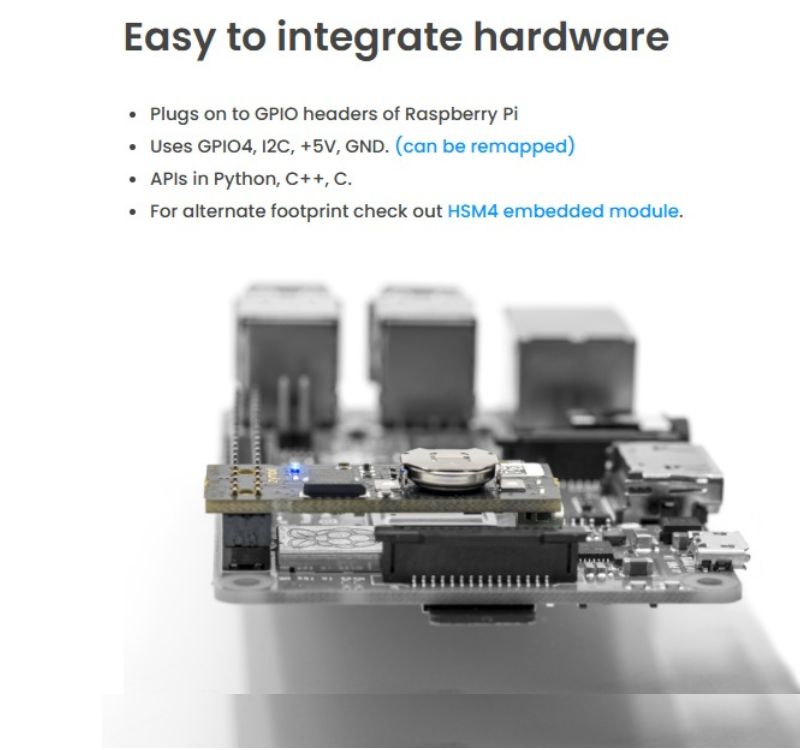
The ZYMKEY4 is a dedicated hardware security module designed specifically for Raspberry Pi. It plugs directly into the GPIO header and provides immediate physical security enhancements without complex integration.
Key features that address the physical vulnerabilities we’ve discussed include:
- Physical Tamper Detection: ZYMKEY4 includes multiple tamper sensors—an accelerometer detects movement or orientation changes, while perimeter tamper circuits can monitor enclosure integrity.
- Key Zeroization: If tampering is detected, ZYMKEY4 can immediately erase sensitive cryptographic keys in a “last gasp” security response, preventing their theft even if the attacker gains access.
- Battery-Backed Security: A coin-cell battery powers the tamper detection circuits and real-time clock even when the Pi is powered off, ensuring continuous protection.
- Secure Boot Support: ZYMKEY4 works with Zymbit’s Bootware to implement secure boot, preventing the loading of unauthorized firmware or operating systems.
- Device Binding: The hardware establishes a unique device identity tied to the specific Raspberry Pi, making cloning or device substitution detectable.
By addressing these key physical vulnerabilities, ZYMKEY4 transforms a standard Raspberry Pi into a tamper-resistant platform suitable for sensitive applications and hostile deployment environments.
Implementing Physical Security in Real-World Deployments

Moving from concept to implementation, here are practical steps for securing Raspberry Pi devices in production environments:
- Assess Physical Risks: Consider where devices will be deployed and what physical threats they might face.
- Implement Hardware Security: Integrate a hardware security module like ZYMKEY4 to provide tamper detection and response.
- Secure the Enclosure: Design tamper-evident or tamper-resistant enclosures appropriate for your threat model.
- Encrypt Sensitive Data: Use the HSM to manage encryption keys for protecting data at rest.
- Establish Secure Boot: Ensure only authorized firmware and operating systems can run on the device.
These measures create layers of protection that work together to secure your Raspberry Pi deployment. For industry-specific implementations, look for our upcoming guides on “Securing Raspberry Pi in Industrial IoT” and “Tamper-Resistant Design for Retail Payment Terminals.”
Frequently Asked Questions
Isn’t encryption enough to protect my data on the Raspberry Pi?
Encryption is essential but insufficient against physical attacks. If an attacker has physical access to your device, they can easily extract encryption keys from memory or modify the system to reveal keys when used. Hardware security modules store keys in tamper-resistant elements that protect them even during physical attacks.
How difficult is it to implement ZYMKEY4 on an existing Pi project?
ZYMKEY4 is designed for easy integration—it plugs directly into the Raspberry Pi’s GPIO header and can be added late in the design cycle. The software integration requires minimal code changes, with Python and C/C++ APIs available. Most projects can implement basic protection in less than a day.
Can I still access GPIO pins with ZYMKEY4 installed?
Yes. While ZYMKEY4 uses some GPIO pins, it passes through most of the pins, allowing you to use them for other purposes. The specific pins used by Zymkey4 are documented, so you can design around them if needed.
What happens if tampering is detected on the ZYMKEY4?
When ZYMKEY4 detects tampering, it can take several configurable actions: erasing cryptographic keys, triggering system alerts, logging the event with a secure timestamp, or even shutting down critical services. This prevents attackers from accessing sensitive data even if they gain physical access to the device.
Is ZYMKEY4 suitable for battery-powered projects?
Yes, but with considerations for power consumption. ZYMKEY4 includes its own battery backup for tamper detection when the main system is powered down. For battery-powered applications, you should evaluate the additional power requirements and potentially implement power management strategies.
Conclusion: From Prototype to Secure Raspberry Pi Product
Physical security for Raspberry Pi transforms a vulnerable compute into a trustworthy platform for secure applications. As we’ve seen, software protections alone cannot defend against determined attackers with physical access to your device.
By implementing hardware-based security with modules like ZYMKEY4, you gain:
- Tamper detection that alerts you to physical breach attempts
- Secure key storage that protects secrets even during attacks
- Device identity that prevents cloning and substitution
- Secure boot capabilities that ensure system integrity
These protections form the foundation of a comprehensive security strategy that addresses both cyber and physical threats. As IoT deployments grow and threats evolve, physical security becomes not just a “nice-to-have” but an essential requirement for any serious Raspberry Pi deployment.
Ready to secure your Raspberry Pi against physical attacks? Explore Zymbit’s ZYMKEY4 and learn how hardware-based security can protect your next project from the threats that software alone can’t address.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.

