TL;DR: You’ll eliminate network security vulnerabilities with zero-trust edge computing devices that continuously self-verify integrity and prevent million-dollar infrastructure breaches autonomously.
Zero-Trust Computing and Securing IoT: Why They Go Together
Zero-trust edge computing represents a fundamental shift in how we secure IoT devices and edge infrastructure. Unlike traditional network-based security models, zero-trust edge computing requires every device to continuously verify its own integrity and prove its trustworthiness before accessing resources or communicating with other systems. This approach becomes critical as billions of connected devices operate in untrusted environments where perimeter security simply isn’t enough. In this comprehensive guide, you’ll learn how self-verifying devices work, why hardware-anchored security is essential, and how modern solutions make implementing zero-trust edge computing accessible for organizations of all sizes.
This post is sponsored by Zymbit.
Key Takeaways
- Zero-trust edge computing eliminates reliance on network perimeters by making each device responsible for its own security verification
- Self-verifying devices use hardware roots of trust to continuously validate their integrity and establish autonomous trust relationships
- Traditional IoT security models fail in distributed environments where devices operate beyond controlled network boundaries
- Hardware security modules provide the foundation for implementing zero-trust principles at the device level
- Modern solutions like Zymbit’s HSM modules make enterprise-grade device security accessible without extensive cryptographic expertise
The $2M Smart City Lesson: When Perimeter Security Fails
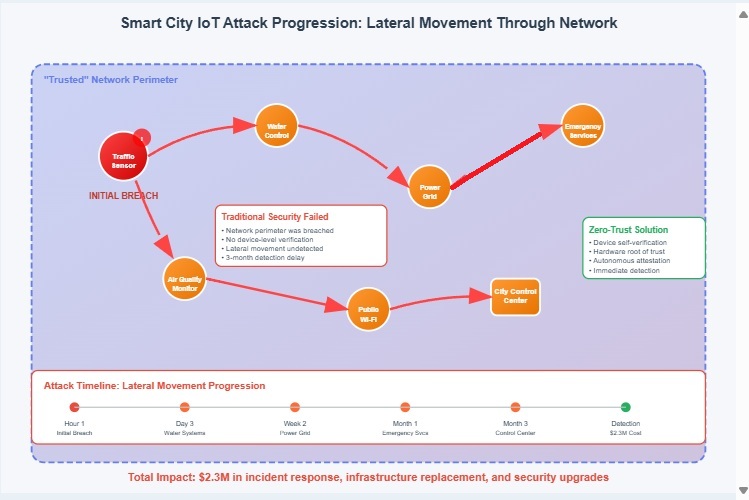
In 2021, a major metropolitan area discovered that sophisticated attackers had compromised dozens of their smart traffic management sensors. The breach wasn’t detected for months, during which time attackers manipulated traffic patterns, extracted sensitive infrastructure data, and potentially accessed broader city systems. The root cause? The city relied entirely on network-level security, assuming that devices within their VPN were trustworthy.
This incident illustrates a critical flaw in traditional IoT security thinking. The compromised sensors had no way to verify their own integrity or prove their trustworthiness to other systems. Once attackers gained initial access through a single vulnerable device, they moved laterally through the network because other systems had no mechanism to validate the authenticity of communications from supposedly “trusted” devices.
The aftermath was costly: $2.3 million in incident response, infrastructure replacement, and security upgrades. More importantly, it highlighted the urgent need for zero-trust edge computing approaches where devices can autonomously verify their own integrity and establish trust relationships without relying on network-level protections.
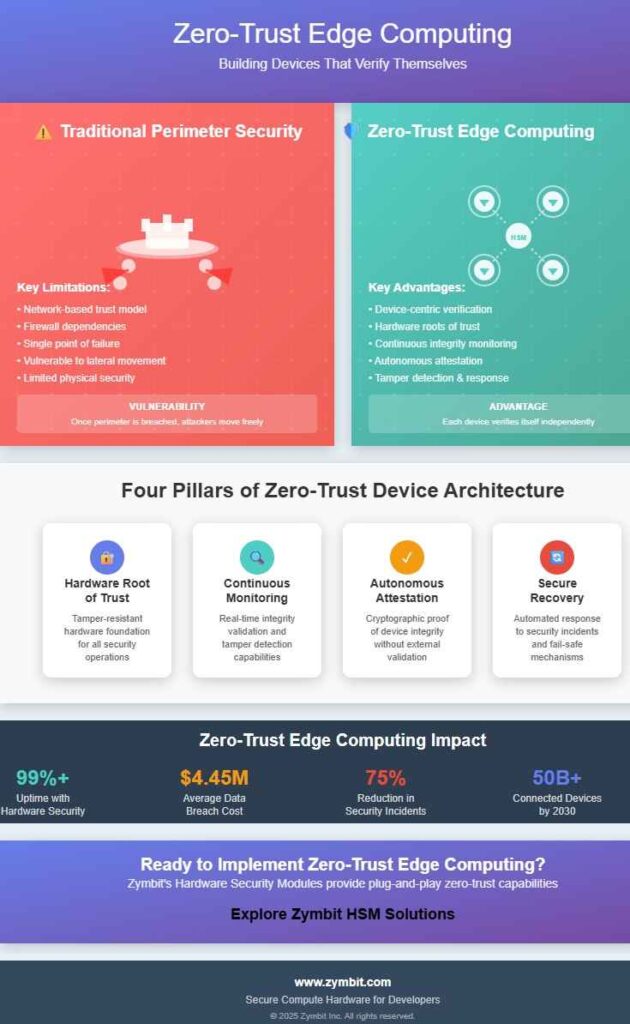
What Makes Zero-Trust Edge Computing Different from Traditional IoT Security?
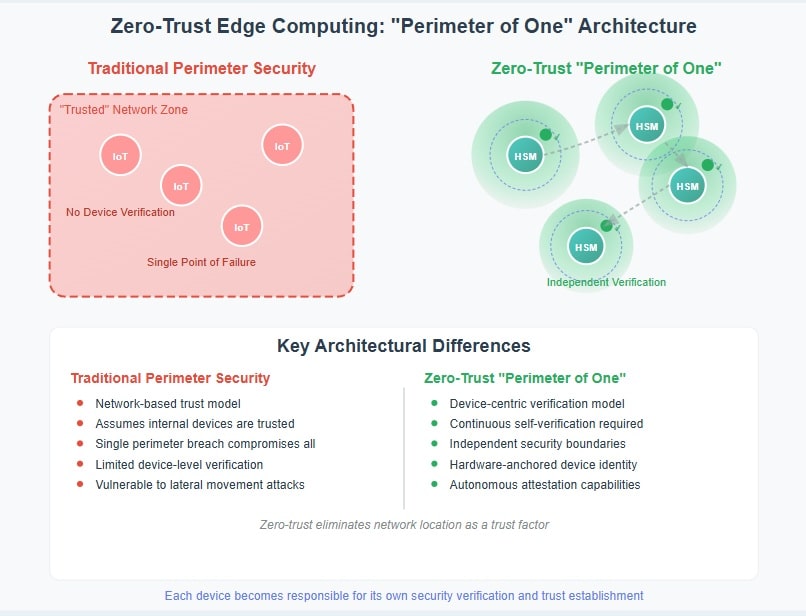
Zero-trust edge computing fundamentally reimagines device security by eliminating the concept of trusted network zones. In traditional models, devices are considered secure if they’re connected to a “trusted” network, protected by firewalls, VPNs, or other perimeter defenses. Zero-trust edge computing rejects this assumption entirely.
Instead of relying on network location to determine trust, zero-trust edge computing requires each device to continuously prove its trustworthiness through self-verification mechanisms. This creates what security experts call a “perimeter of one” – where every device becomes its own security boundary, responsible for validating its own integrity and the authenticity of its communications.
The shift is particularly critical for edge computing deployments where devices operate in physically accessible locations, have intermittent network connectivity, and must function autonomously for extended periods. In these environments, traditional network-based security controls simply cannot provide adequate protection against sophisticated attacks or physical tampering.
Why Do Traditional IoT Security Models Fail at the Edge?
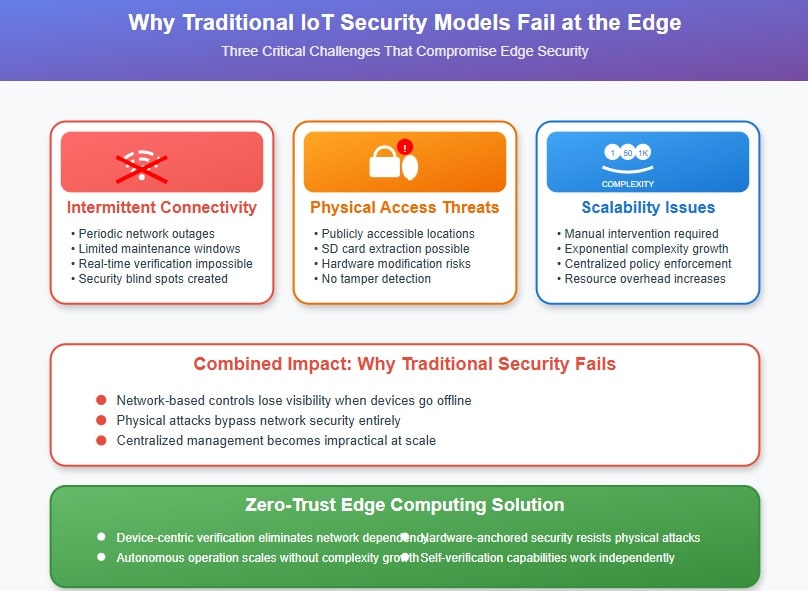
Traditional IoT security approaches were designed for controlled environments where devices operate within well-defined network perimeters. However, edge computing fundamentally challenges these assumptions by placing devices in untrusted locations where physical access, network reliability, and environmental conditions cannot be guaranteed.
Network connectivity limitations represent one of the most significant challenges. Edge devices often operate with intermittent connectivity or during specific maintenance windows, making real-time verification with centralized security services impractical. When a device loses network connectivity, traditional security models lose visibility and control, creating security blind spots that attackers can exploit.
Physical accessibility concerns compound these challenges significantly. Unlike data center equipment protected by multiple layers of physical security, edge devices often operate in publicly accessible locations or minimally secured facilities. Attackers can potentially access devices directly, extract storage media, or modify hardware components – attacks that network-based security measures cannot detect or prevent.
The scalability problem becomes apparent when managing hundreds or thousands of distributed devices. Traditional security models that rely on centralized policy enforcement and monitoring quickly become unwieldy when applied to large-scale edge deployments where manual intervention for security incidents is impractical or impossible.
How Do Self-Verifying Devices Establish Trust Autonomously?
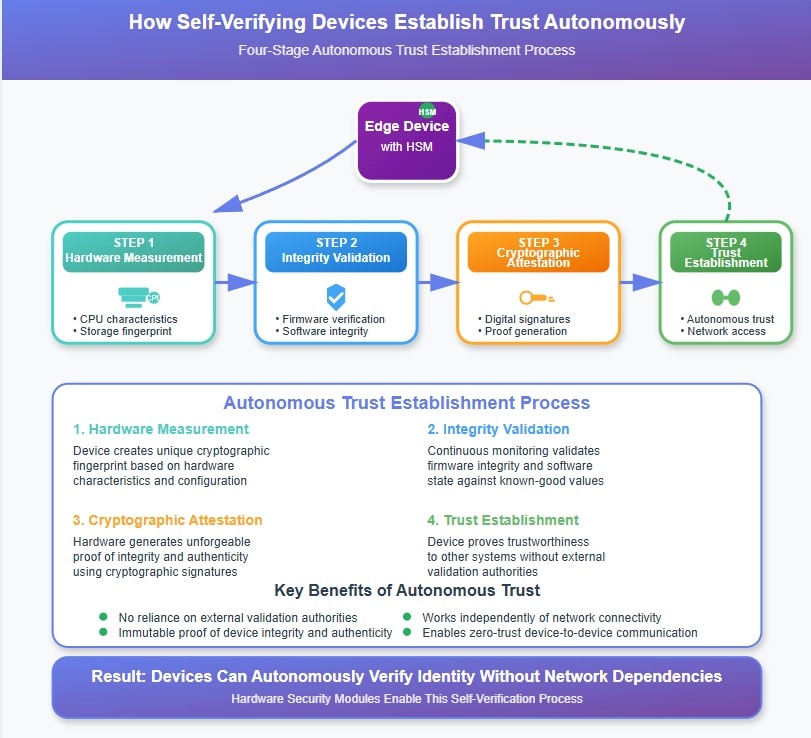
Self-verifying devices solve the fundamental challenge of establishing trust without relying on external authorities or network-based validation systems. These devices implement autonomous trust mechanisms that continuously validate their own integrity and can prove their trustworthiness to other systems through cryptographic attestation.
The foundation of self-verification lies in measured identity – a process where devices create unique cryptographic fingerprints based on their hardware characteristics, firmware configurations, and operational state. This measured identity becomes immutable proof of the device’s authentic state, enabling it to demonstrate its integrity to other systems without requiring external validation.
Continuous integrity monitoring ensures that devices can detect unauthorized changes to their software, configuration, or physical state. When combined with secure response mechanisms, this enables devices to automatically take protective actions – such as isolating themselves from networks or erasing sensitive data – when tampering is detected.
The autonomous nature of this approach is crucial for edge computing scenarios where devices must operate independently for extended periods. Rather than waiting for external systems to verify their status, self-verifying devices can make trust decisions locally while providing cryptographic proof of their integrity to other systems when connectivity is available.
What Are the Four Pillars of Zero-Trust Device Architecture?
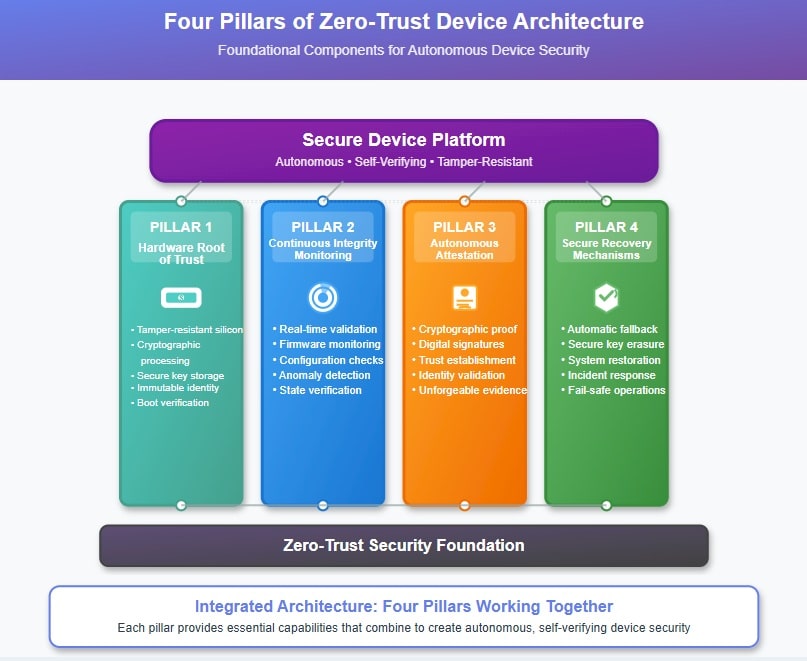
Zero-trust device architecture rests on four foundational pillars that work together to enable autonomous security verification and trust establishment. Understanding these pillars is essential for implementing effective zero-trust edge computing solutions.
Hardware Root of Trust serves as the immutable foundation for all security operations. This specialized hardware component, typically implemented as a hardware security module (HSM) or trusted platform module (TPM), provides tamper-resistant key storage, cryptographic processing capabilities, and secure boot verification. The hardware root of trust ensures that fundamental security operations cannot be compromised even if the main system software is attacked.
Continuous Integrity Monitoring extends beyond traditional periodic security scans to provide real-time validation of device state. This includes monitoring firmware integrity, configuration changes, software modifications, and physical tampering attempts. The continuous nature ensures that security breaches are detected immediately rather than during scheduled maintenance windows.
Autonomous Attestation enables devices to prove their trustworthiness to other systems without requiring centralized validation authorities. Through cryptographic techniques, devices can generate unforgeable proof of their integrity state, software versions, and operational characteristics. This proof can be validated by other systems or services to establish trust relationships dynamically.
Secure Recovery Mechanisms ensure that devices can respond appropriately to detected security incidents or failures. This includes automatic fallback to known-good configurations, secure erasure of sensitive data when tampering is detected, and fail-safe communication with management systems to report security events.
Where Is Zero-Trust Edge Computing Most Critical in Real-World Applications?
Zero-trust edge computing proves most valuable in applications where devices operate in untrusted environments, handle sensitive data, or control critical infrastructure. These scenarios highlight why traditional network-based security approaches are insufficient for modern edge computing deployments.
Industrial automation represents one of the most compelling use cases for zero-trust edge computing. Manufacturing facilities deploy thousands of sensors, controllers, and monitoring devices that must operate reliably in harsh environments while protecting valuable intellectual property and operational data. Zymbit’s partnership with Sfera Labs demonstrates this application perfectly – their Strato Pi Max industrial controller integrates Zymbit’s Secure Compute Module to provide hardware-anchored security for critical manufacturing applications.
Smart infrastructure and utility deployments face similar challenges, with devices distributed across vast geographic areas and often accessible to the public. Water treatment facilities, power grid components, and transportation systems require devices that can verify their own integrity and detect tampering attempts autonomously. The consequences of compromised infrastructure devices extend far beyond data breaches to potential physical safety risks.
Financial and payment terminals present another critical application area where zero-trust edge computing provides essential protection. Point-of-sale systems, ATMs, and mobile payment devices handle sensitive financial data while operating in publicly accessible locations. These devices must prove their authenticity to prevent card skimming attacks and protect customer financial information.
Healthcare monitoring devices increasingly operate outside traditional clinical environments, collecting sensitive patient data in homes, assisted living facilities, and remote healthcare settings. Zero-trust edge computing ensures these devices maintain privacy protections while enabling secure communication with healthcare providers and electronic health record systems.
How Do Hardware Security Modules Enable Zero-Trust Edge Computing?
Hardware Security Modules (HSMs) provide the foundational technology that makes zero-trust edge computing practical and secure. Unlike software-based security measures that can be compromised through various attack vectors, HSMs implement security functions in dedicated, tamper-resistant hardware that maintains its integrity even when the host system is compromised.
The isolation provided by HSMs creates a secure boundary that software attacks cannot breach. Cryptographic keys, device identities, and security operations remain protected within the HSM even if the main processor or operating system is compromised. This isolation is crucial for zero-trust edge computing because it ensures that fundamental trust mechanisms remain intact regardless of other system vulnerabilities.
Zymbit’s approach to hardware security exemplifies how modern HSMs enable zero-trust edge computing. The HSM4 module provides comprehensive security features including secure key storage, tamper detection, and cryptographic processing in a compact form factor that integrates easily with edge computing platforms like Raspberry Pi. For applications requiring advanced cryptographic capabilities, the HSM6 offers expanded key storage and hardware wallet functionality suitable for blockchain and cryptocurrency applications.
Bootware software complements Zymbit’s hardware modules by providing secure boot, encrypted storage, and fail-safe update mechanisms. This integrated approach ensures that devices can maintain their security posture throughout their operational lifecycle while providing the autonomous verification capabilities essential for zero-trust edge computing.
The combination of hardware-anchored security and intelligent software management creates a comprehensive solution that addresses the full spectrum of edge computing security challenges without requiring extensive cryptographic expertise from development teams.
What Challenges Must Organizations Overcome to Implement Zero-Trust Edge Computing?
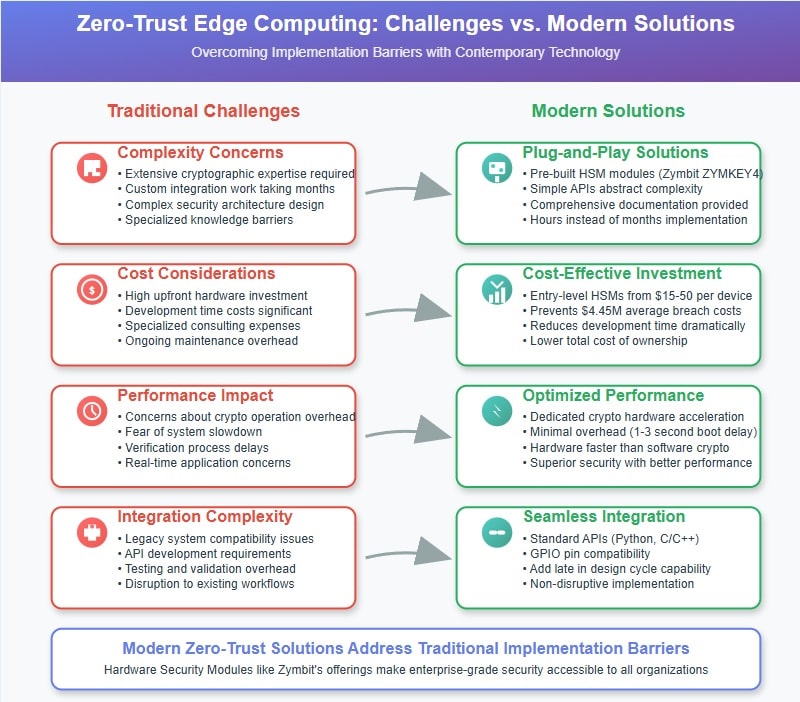
Organizations considering zero-trust edge computing often face several implementation challenges that can seem daunting without proper understanding and planning. However, modern solutions have significantly reduced these barriers, making enterprise-grade security accessible to organizations of all sizes.
Complexity concerns typically top the list of implementation challenges. Traditional approaches to hardware security required extensive cryptographic expertise and custom integration work that could take months to complete. However, modern solutions like Zymbit’s HSM modules are designed for plug-and-play integration, with comprehensive documentation and example implementations that enable rapid deployment even for teams without specialized security backgrounds.
Cost considerations often create hesitation around hardware security investments. While HSMs do add to the bill of materials cost – typically $40-125 per device depending on requirements – this investment must be evaluated against the potential costs of security breaches, operational disruptions, and compliance violations. The total cost of ownership often favors hardware security when all factors are considered.
Performance impact concerns stem from misconceptions about hardware security overhead. Modern HSMs are designed to provide security functions without significantly impacting device performance. Cryptographic operations performed in dedicated hardware are often faster than software implementations while providing superior security guarantees.
Integration complexity has been dramatically reduced through standardized APIs and comprehensive development tools. Zymbit’s approach exemplifies this trend, providing Python and C/C++ APIs that abstract complex security operations into simple function calls that developers can integrate quickly into existing applications.
What Does the Future Hold for Autonomous Device Security?
The evolution toward fully autonomous device security represents one of the most significant trends in edge computing and IoT development. As devices become more sophisticated and deployments scale to billions of connected endpoints, the need for self-sufficient security mechanisms becomes increasingly critical.
Artificial intelligence integration will enhance device security capabilities by enabling more sophisticated threat detection and response mechanisms. AI-powered security agents running on edge devices will be able to identify novel attack patterns, adapt security policies dynamically, and coordinate responses across device fleets without requiring centralized management.
Blockchain and distributed ledger technologies are beginning to intersect with device security in interesting ways. Zero-trust edge computing provides the foundation for devices to participate in blockchain networks securely, enabling new applications like autonomous micro-transactions, decentralized identity verification, and peer-to-peer device authentication.
The concept of self-sovereign devices – devices that can establish and maintain their own security policies without external dependencies – represents the ultimate evolution of zero-trust edge computing. These devices will be capable of making complex security decisions autonomously while providing cryptographic proof of their actions to external systems when required.
Standards development and regulatory frameworks are beginning to recognize the importance of device-level security. Future compliance requirements will likely mandate hardware-anchored security for devices in critical industries, making zero-trust edge computing not just a best practice but a regulatory necessity.
Conclusion: Building the Foundation for Trustworthy Edge Computing
Zero-trust edge computing represents more than just a security enhancement – it’s a fundamental reimagining of how devices establish and maintain trust in distributed computing environments. As organizations increasingly rely on edge computing for critical operations, the ability to verify device integrity autonomously becomes essential for maintaining security, compliance, and operational reliability.
The shift from network-based security models to device-centric verification addresses the core challenges of modern edge computing: intermittent connectivity, physical accessibility, and scale. By implementing hardware-anchored security through solutions like Zymbit’s HSM modules and Bootware software, organizations can deploy edge computing solutions with confidence, knowing that devices can protect themselves and prove their trustworthiness regardless of their operating environment.
The investment in zero-trust edge computing technology pays dividends through reduced security risks, improved operational reliability, and enhanced compliance posture. As edge computing continues to expand across industries, organizations that embrace zero-trust principles early will be better positioned to leverage these technologies securely and effectively.
Ready to implement zero-trust edge computing in your organization? Visit Zymbit’s website to learn more about hardware-anchored security solutions and discover how HSM modules can transform your edge computing deployments from vulnerable endpoints into self-verifying, trustworthy devices.
Frequently Asked Questions
What’s the difference between zero-trust networking and zero-trust edge computing?
Zero-trust networking focuses on verifying users and applications before granting network access, while zero-trust edge computing extends these principles to the device level. In zero-trust edge computing, devices themselves must prove their integrity and trustworthiness continuously, not just authenticate to networks.
Can existing IoT devices be upgraded to support zero-trust edge computing?
Some devices can be retrofitted with external hardware security modules, but the most effective implementations integrate security hardware during the design phase. Devices without hardware security foundations will have limited zero-trust capabilities compared to purpose-built solutions.
How does zero-trust edge computing impact device performance?
Modern hardware security modules are designed to provide security functions with minimal performance impact. Cryptographic operations performed in dedicated hardware are often faster than software implementations while providing superior security guarantees.
What industries benefit most from zero-trust edge computing?
Industries with distributed critical infrastructure benefit most, including manufacturing, utilities, healthcare, financial services, and smart cities. Any application where devices operate in untrusted environments or handle sensitive data can benefit from zero-trust edge computing principles.
Is zero-trust edge computing cost-effective for small deployments?
Yes, hardware security modules typically add $40-125 per device, but this investment prevents much larger costs from security breaches, compliance violations, and operational disruptions. The total cost of ownership often favors hardware security even for small deployments.
How does zero-trust edge computing handle device updates and maintenance?
Zero-trust devices can verify update authenticity using cryptographic signatures and hardware-anchored trust mechanisms. Modern solutions like Zymbit’s Bootware provide fail-safe update processes with automatic rollback capabilities if updates fail or are tampered with.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.

