TL;DR: You’ll eliminate your network’s single point of failure with LoRaWAN gateway security that prevents cybercriminals from hijacking entire IoT infrastructures through hardware-based protection.
Why Consider LoRaWan Gateway Security?
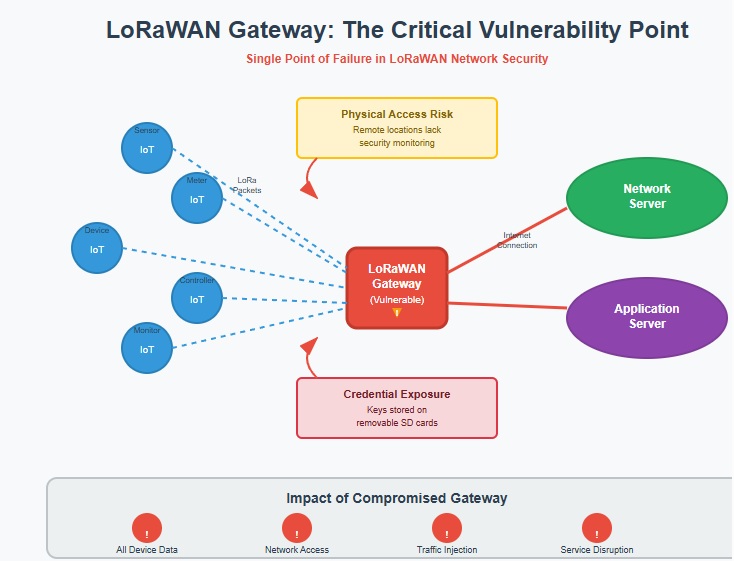
Let’s consider the following: A precision agriculture company deployed 200 smart irrigation sensors across its 10,000-acre operation. They thought their biggest challenge would be optimizing water usage. Instead, they discovered that their unsecured LoRaWAN gateway had become a backdoor for cybercriminals who gained control of their entire irrigation system. This scenario highlights a critical oversight in IoT deployments: while organizations focus on securing individual devices, they often neglect the gateway —the single point of failure that can compromise an entire LoRaWAN network.
LoRaWAN gateway security represents one of the most overlooked yet critical aspects of IoT network protection. As the bridge between end devices and network infrastructure, gateways process all communication within a LoRaWAN network, making them attractive targets for malicious actors. Understanding and implementing proper security measures for these critical components can mean the difference between a robust, trustworthy IoT deployment and a network vulnerable to data theft, service disruption, and unauthorized access.
Note: This post is sponsored by Zymbit
Key Takeaways
- LoRaWAN gateways are single points of failure that can compromise entire IoT networks if left unsecured
- Physical vulnerabilities in remote gateway deployments create significant attack surfaces for malicious actors
- Hardware-based security solutions provide the foundation for protecting LoRaWAN infrastructure against both digital and physical threats
- Implementing proper authentication, encryption, and tamper detection transforms vulnerable gateways into secure network assets
- Zymbit’s hardware security modules offer plug-and-play solutions for hardening Raspberry Pi-based LoRaWAN deployments
Understanding LoRaWAN Gateway Security Vulnerabilities in IoT Networks
MJ Prompt: A detailed technical diagram showing a LoRaWAN network topology with a central gateway connecting multiple IoT devices to cloud infrastructure, with red warning symbols highlighting potential vulnerability points –ar 16:9 –style technical
LoRaWAN gateways serve as the critical communication hub in Long Range Wide Area Network deployments, forwarding packets from end devices to the network server while maintaining the delicate balance between range, power consumption, and data throughput. However, this central role also makes gateways the most attractive target for attackers seeking to compromise IoT networks. Unlike end devices that communicate sporadically and have limited processing power, gateways maintain constant connectivity to both the local LoRa network and internet infrastructure.
The security challenges facing LoRaWAN deployments stem from the protocol’s design philosophy, which prioritizes low power consumption and wide area coverage over robust security measures. While the LoRa Alliance has implemented security features including end-to-end encryption and authentication mechanisms, many of these protections focus on the communication between end devices and the network server, leaving gateways as potential weak links in the security chain. This gap becomes particularly problematic when gateways are deployed in remote, unattended locations where physical security cannot be guaranteed.
Modern IoT applications increasingly rely on LoRaWAN technology for smart cities, industrial monitoring, and agricultural automation, making LoRaWAN gateway security more critical than ever. As these deployments scale from pilot projects to production environments, the potential impact of compromised gateways grows exponentially. A single compromised gateway can affect hundreds or thousands of connected devices, potentially disrupting critical infrastructure or exposing sensitive operational data.
How Do Physical Threats Compromise LoRaWAN Gateway Security?
Physical security represents one of the most significant vulnerabilities in LoRaWAN gateway deployments, particularly when gateways are installed in remote or publicly accessible locations. Unlike network servers housed in secure data centers, LoRaWAN gateways must be positioned strategically to provide optimal coverage, often placing them in locations where physical access control is minimal or nonexistent. This exposure creates opportunities for malicious actors to directly manipulate gateway hardware, extract credentials, or install unauthorized monitoring equipment.
The most common attack vector involves accessing the gateway’s storage media, particularly in Raspberry Pi-based implementations where SD cards can be easily removed and analyzed. These storage devices typically contain network credentials, encryption keys, and configuration data in unprotected formats. An attacker with brief physical access can clone the entire SD card, analyze the data offline, and potentially gain access to the broader LoRaWAN network without triggering any security alerts. This vulnerability is compounded by the fact that many gateway deployments use default credentials or store authentication information in plain text configuration files.
Environmental factors further complicate physical security in LoRaWAN deployments. Gateways installed on rooftops, utility poles, or in agricultural fields must withstand weather conditions while remaining accessible for maintenance. Standard weather-resistant enclosures provide protection from the elements but offer little resistance to determined attackers. The challenge becomes balancing accessibility for legitimate maintenance with security against unauthorized access, particularly in deployments where site visits for monitoring are infrequent.
What Makes Credential Theft So Dangerous in LoRaWAN Networks?
Credential theft represents a particularly insidious threat to LoRaWAN gateway security because compromised credentials can provide persistent, undetected access to network infrastructure. LoRaWAN gateways typically store multiple types of sensitive information, including network session keys, server authentication certificates, and device activation credentials. When these credentials are compromised, attackers can impersonate legitimate gateways, intercept communication between end devices and network servers, or inject malicious traffic into the network.
The architecture of LoRaWAN networks makes credential theft especially damaging because gateways are trusted entities within the network topology. The network server assumes that traffic forwarded by registered gateways is legitimate, creating opportunities for attackers with compromised credentials to manipulate data flows without detection. This trust relationship means that a single compromised gateway can potentially affect the integrity of data from hundreds of connected devices, making credential protection a critical security priority.
Key management presents ongoing challenges in LoRaWAN deployments, particularly at scale. Many implementations rely on static credentials that are difficult to rotate without disrupting network operations. When credentials are stored in vulnerable locations such as unencrypted configuration files on SD cards, the process of credential rotation becomes even more complex, as it requires physical access to each gateway. This operational challenge often leads to organizations postponing credential updates, leaving known vulnerabilities in place for extended periods.
Why Does Firmware Security Matter for LoRaWAN Gateways?
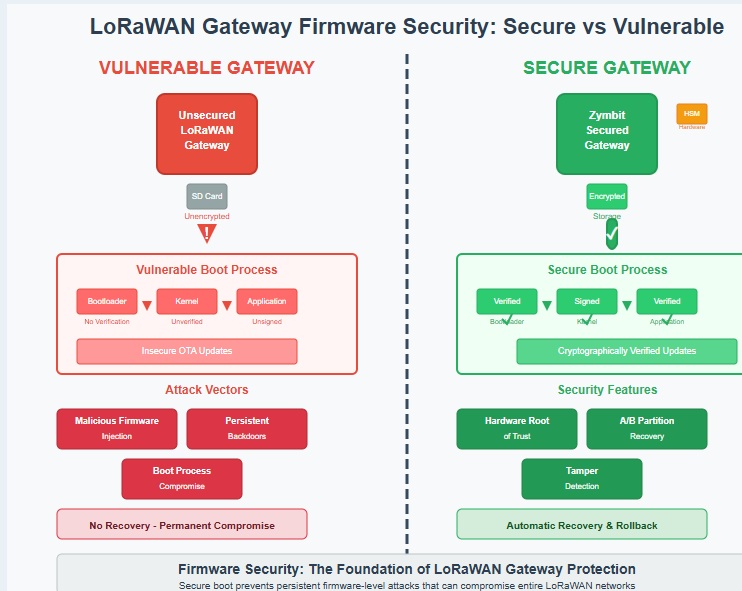
Firmware security in LoRaWAN gateways represents a critical but often overlooked aspect of network protection. Unlike application-level security measures that can be updated or patched relatively easily, firmware-level compromises can provide attackers with persistent access that survives system reboots and software updates. The challenge is particularly acute in Raspberry Pi-based gateway implementations, where standard boot processes lack secure verification mechanisms and firmware updates often occur through vulnerable channels.
The absence of secure boot capabilities in most LoRaWAN gateway deployments creates opportunities for attackers to inject malicious code at the firmware level. Without cryptographic verification of boot components, there’s no guarantee that the software running on a gateway is authentic or unmodified. This vulnerability becomes especially concerning when gateways are deployed in remote locations where unauthorized access might go undetected for extended periods. Malicious firmware can potentially log all network traffic, extract encryption keys, or create backdoors for future access.
Firmware update mechanisms in LoRaWAN deployments often prioritize convenience over security, creating additional attack vectors. Many gateways accept firmware updates over wireless connections without proper authentication or integrity verification. This design choice, while operationally convenient, allows attackers to potentially distribute malicious firmware across entire gateway deployments. The lack of rollback mechanisms in many implementations means that corrupted or malicious firmware updates can permanently compromise gateway functionality.
How Can Hardware Security Modules Protect LoRaWAN Infrastructure?
Hardware Security Modules represent a fundamental shift in approach to LoRaWAN gateway security, moving critical security functions from vulnerable software implementations to dedicated, tamper-resistant hardware. Unlike traditional software-based security measures that can be compromised through various attack vectors, HSMs provide a physically isolated environment for key storage, cryptographic operations, and security verification. This hardware-based approach addresses many of the fundamental vulnerabilities that plague standard gateway deployments.
Zymbit’s HSM4 and HSM6 modules offer specific solutions for LoRaWAN gateway security challenges. The HSM4 provides essential security features including secure key storage, tamper detection, and encrypted communication interfaces, making it ideal for standard LoRaWAN deployments where basic security hardening is required. The module’s ability to detect physical tampering and respond with key erasure provides protection against the physical access vulnerabilities that commonly affect remote gateway installations.
For more complex LoRaWAN deployments requiring advanced key management capabilities, the HSM6 offers expanded cryptographic functionality with support for 512 private/public key pairs and hardware wallet features. This enhanced capacity becomes particularly valuable in multi-network gateway implementations or scenarios requiring complex authentication hierarchies. The HSM6’s support for BIP standards also enables integration with blockchain-based IoT applications, expanding the security foundation beyond traditional LoRaWAN protocols.
What Role Does Secure Boot Play in LoRaWAN Gateway Security Protection?
Secure boot functionality addresses one of the most critical vulnerabilities in LoRaWAN gateway security by ensuring that only authenticated, unmodified firmware can execute on gateway hardware. Zymbit’s Bootware solution provides comprehensive secure boot capabilities specifically designed for Raspberry Pi-based gateway implementations, creating a verified chain of trust from hardware initialization through application startup. This approach prevents the firmware-level attacks that can provide persistent, undetected access to gateway functionality.
The A/B partition system implemented by Bootware offers particular advantages for LoRaWAN gateway deployments, where network availability is critical. By maintaining two complete system images and only switching to updated versions after successful verification, gateways can receive firmware updates without risking service interruption. If an update fails verification or causes system instability, the automatic rollback functionality ensures that gateways remain operational while providing diagnostic information for troubleshooting.
Cryptographic verification of all boot components ensures that the integrity of gateway software can be trusted throughout the operational lifecycle. Each component in the boot chain is verified against cryptographic signatures stored in the hardware security module, preventing the execution of modified or malicious code. This verification process extends beyond the boot sequence to include runtime monitoring capabilities that can detect and respond to unauthorized changes in system behavior.
How Do Tamper Detection Features Enhance LoRaWAN Gateway Security?
Tamper detection represents a crucial physical security layer for LoRaWAN gateways deployed in unattended locations where traditional access control measures are impractical. Zymbit’s hardware security modules include multiple tamper detection mechanisms, including accelerometers that detect movement or orientation changes and perimeter circuits that monitor enclosure integrity. These sensors provide real-time monitoring capabilities that can detect unauthorized access attempts even when the gateway is powered off, thanks to battery-backed security circuits.
The response mechanisms available through tamper detection systems offer flexible protection options tailored to different deployment scenarios. In high-security applications, tamper events can trigger immediate key erasure, ensuring that sensitive credentials cannot be extracted even if the gateway is physically compromised. For less critical deployments, tamper detection can generate alerts and log events while maintaining operational capability, allowing security teams to investigate potential threats without disrupting network operations.
Integration of tamper detection with broader security monitoring systems enables comprehensive threat response for LoRaWAN deployments. When tamper events are detected, automated systems can isolate affected gateways from the network, rotate credentials, and initiate forensic analysis procedures. This automated response capability is particularly valuable in large-scale deployments where manual monitoring of individual gateways is impractical.
Which Zymbit Solutions Best Fit Different LoRaWAN Deployment Scenarios?
Selecting the appropriate Zymbit security solution for LoRaWAN gateway deployments depends on specific requirements including scale, security level, and operational complexity. For standard LoRaWAN deployments where basic security hardening is the primary concern, the HSM4 provides essential security features including secure key storage, tamper detection, and encrypted communication interfaces. This solution is particularly well-suited for smart city applications, agricultural monitoring, and industrial IoT deployments where straightforward security enhancement is required without complex key management requirements.
The HSM6 offers advanced capabilities for LoRaWAN deployments requiring sophisticated key management or multi-network functionality. With support for 512 private/public key pairs and hardware wallet features, the HSM6 can handle complex authentication scenarios, multi-tenant gateway deployments, or integration with blockchain-based IoT applications. This enhanced capability makes it ideal for large-scale industrial deployments, critical infrastructure monitoring, or applications requiring compliance with stringent security standards.
Zymbit’s Secure Edge Node options provide pre-integrated, production-ready platforms for organizations seeking turnkey LoRaWAN gateway solutions. These platforms combine compute capabilities with integrated security features, eliminating the complexity of hardware integration while providing enterprise-grade security from deployment. The Secure Edge Nodes are particularly valuable for organizations with limited technical resources or those requiring rapid deployment of secure gateway infrastructure.
Frequently Asked Questions
How vulnerable are LoRaWAN gateways to cyber attacks?
LoRaWAN gateways are highly vulnerable to both physical and digital attacks due to their central role in network communication and frequent deployment in unsecured locations. Without proper security measures, attackers can extract credentials, inject malicious traffic, or gain access to entire IoT networks through compromised gateways.
What makes Raspberry Pi-based LoRaWAN gateways particularly insecure?
Standard Raspberry Pi implementations lack secure boot capabilities, store credentials on easily removable SD cards, and have no tamper detection features. These vulnerabilities make them attractive targets for attackers seeking to compromise LoRaWAN networks through physical access or credential theft.
How does hardware-based security improve LoRaWAN gateway security protection?
Hardware Security Modules provide tamper-resistant storage for encryption keys, implement secure boot verification, and offer physical tamper detection capabilities. This approach moves critical security functions away from vulnerable software implementations to dedicated, protected hardware environments.
Can existing LoRaWAN gateways be retrofitted with better security?
Yes, Zymbit’s HSM modules can be easily integrated with existing Raspberry Pi-based LoRaWAN gateways through GPIO connections. This retrofit approach allows organizations to enhance security without completely replacing their gateway infrastructure.
What happens if a secured LoRaWAN gateway is physically tampered with?
Zymbit’s tamper detection systems can respond to physical interference by erasing encryption keys, logging security events, or alerting security teams. This ensures that sensitive credentials cannot be extracted even if attackers gain physical access to gateway hardware.
How does secure boot protect LoRaWAN gateway firmware?
Secure boot verifies the cryptographic signatures of all firmware components before execution, preventing malicious or modified code from running on gateway hardware. Combined with A/B partition systems, this ensures that gateways can safely receive updates while maintaining operational availability through automatic rollback capabilities.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.
