Why Do You Need More than Software Encryption?
When you implement software encryption to make your Raspberry Pi secure in IoT applications, you’re deploying only one layer of what should be a multi-faceted security architecture. The computational constraints of these SBCs often force tradeoffs between robust cryptographic protocols and performance overhead. Neither AES-256 nor elliptic curve algorithms can mitigate physical access vulnerabilities or side-channel attacks targeting your device. The question isn’t whether encryption works—it’s whether it sufficiently addresses the actual threat vectors in your deployment scenario.
Key Takeaways
- Software encryption alone cannot protect Raspberry Pi devices when attackers gain physical access to USB ports or microSD cards.
- Encryption introduces computational overhead that impacts system performance and power consumption, requiring a balance for resource-constrained IoT devices.
- Key management remains a significant vulnerability, as software-based key storage can be compromised through various extraction techniques.
- Complete IoT security requires layered approaches including TLS for communications, physical security measures, and regular security monitoring.
- Regulatory compliance with standards like PSTI and ETSI EN 303 645 requires encryption as part of a comprehensive security architecture for IoT deployments.
The Real Security Limits of Software Encryption on Raspberry Pi
While software encryption provides valuable security mechanisms for Raspberry Pi deployments, it operates within distinct technical constraints that implementers must acknowledge.
The computational overhead introduced by encryption algorithms—particularly asymmetric variants—can degrade system performance and increase power consumption, creating potential bottlenecks in real-time applications.
Key management presents perhaps the most significant vulnerability vector. Without hardware security modules, your encryption implementation relies on software-based key storage that’s inherently susceptible to extraction attacks. This represents a fundamental security paradox: encryption protects your data, but the keys protecting that encryption remain exposed. The physical access vulnerability allows attackers to simply remove the SD card and read its contents unauthorized.
The cornerstone weakness of Pi-based encryption: your data fortress is only as secure as its software-stored keys.
Additionally, encryption overhead scales with data throughput, potentially compromising responsiveness in bandwidth-intensive IoT applications.
While libraries like mbed TLS optimize cryptographic operations, they can’t eliminate the fundamental resource limitations of the Pi’s architecture when implementing robust encryption protocols. Implementing SSH key-based authentication can significantly enhance your Raspberry Pi’s security posture when network access is required. Approximately 33% of computers are affected by some form of malware that could compromise your encryption implementation. Incorporating multiple layers of defense, such as using both encryption and network firewalls, creates a more comprehensive security posture than relying on encryption alone.
Physical Access Vulnerabilities No Encryption Can Solve
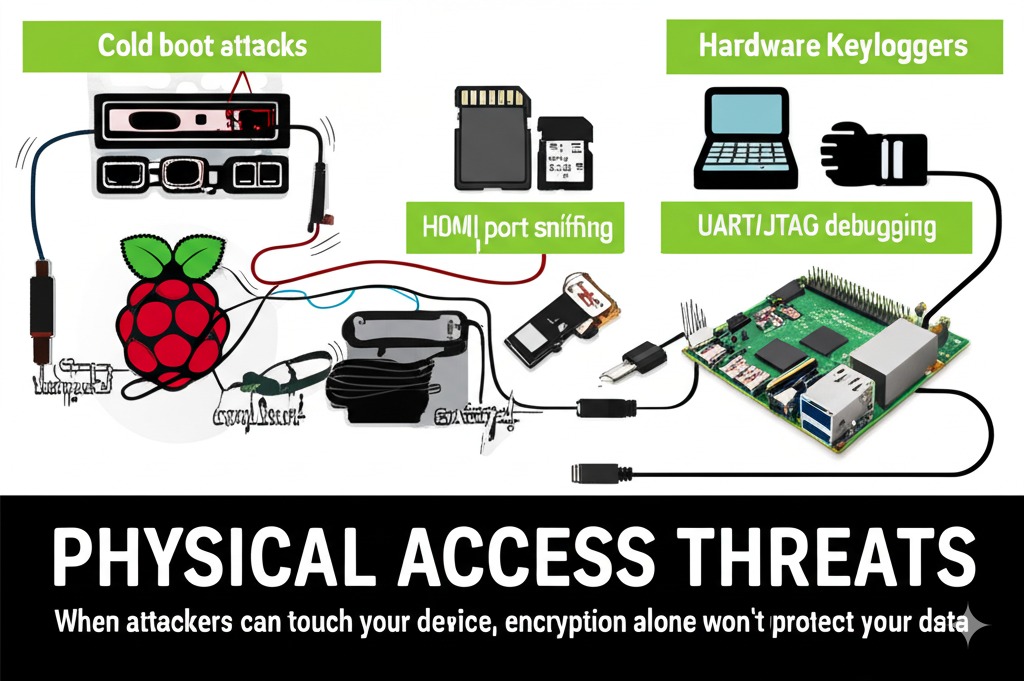
While your Raspberry Pi’s software encryption protocols may robustly safeguard data at rest, they’re rendered ineffective when an adversary gains physical access to exploit USB port backdoors, perform MicroSD card extraction, or leverage GPIO pin vulnerabilities.
Your device’s exposed USB interfaces present attack vectors for malicious peripherals that can execute privilege escalation or BadUSB attacks, bypassing encryption safeguards entirely. Effective device management is critical for preventing unauthorized physical access to IoT devices. Small IoT devices like Raspberry Pis are particularly vulnerable due to their easy concealment if stolen from their deployment location.
Physical access threats extend to GPIO pin exploitation where attackers can intercept unencrypted UART communications or perform voltage glitching to compromise your Pi’s security perimeter regardless of encryption implementation strength.
USB Port Backdoors
Despite sophisticated software encryption protocols, USB ports on Raspberry Pi devices represent critical hardware backdoors that can’t be mitigated through cryptographic means alone.
When attackers gain physical access to your device, they can exploit USB security measures by connecting malicious peripherals that masquerade as legitimate HID devices.
These HID device vulnerabilities enable threat actors to inject commands, extract data, or establish persistent backdoors—all while bypassing your encryption safeguards. A compromised keyboard or flash drive can execute pre-programmed attack sequences within seconds of connection. Devices like the Raspberry Pi Zero W can be configured to act as keyboards and automatically inject malicious keystrokes when connected to a victim’s computer.
Additionally, power-back feeding techniques through USB hubs create additional attack vectors that circumvent standard protective measures. Companies can be legally compelled to implement backdoor capabilities for surveillance purposes in firmware components.
To counter unauthorized device access and physical access risks, consider implementing hub-ctrl utilities to disable power to unused ports, applying kernel-level USB restrictions, and establishing robust physical security controls around your IoT deployment environment. Installing Fail2Ban tools can provide additional protection against brute force attacks targeting your Raspberry Pi’s physical interfaces.
MicroSD Card Tampering
Even sophisticated encryption protocols can’t mitigate the fundamental vulnerability inherent in Raspberry Pi’s removable storage architecture.
Your microSD card represents a critical attack vector—trivially extracted, mounted externally, and compromised without triggering tampering detection mechanisms.
Adversaries with momentary physical access can execute cold boot attacks extracting encryption keys from RAM, clone entire storage volumes, or simply substitute your card with a preconfigured malicious image.
The absence of hardware security modules (HSMs) compounds this vulnerability, as cryptographic keys remain exposed in software-accessible memory regions.
Raspbian’s lack of intrusion detection leaves your system blind to hardware-level breaches. Individuals who gain access can easily edit system files that grant them root privileges to the device.
Without secure boot implementations protecting the entire boot chain, attackers can modify bootloaders to circumvent encryption entirely.
Physical access effectively renders your software encryption irrelevant, regardless of algorithmic strength or key management protocols. Devices like Raspberry Pi are increasingly exploited for data breaches and malware installation when implemented in IoT environments without proper physical security.
GPIO Pin Exploitation
Beyond the domain of software-based protections, Raspberry Pi’s General-Purpose Input/Output (GPIO) interface constitutes a pervasive security perimeter breach that encryption algorithms can’t address. Physical access threats enable adversaries to exploit shared pin vulnerabilities through signal injection risks, bypassing all software safeguards. Configuring proper access level permissions through udev rules is essential for basic GPIO security on Raspberry Pi systems. Multiple applications can read GPIO states simultaneously without causing blocking or interference with control systems. Input validation mechanisms should be implemented to prevent malicious code execution through GPIO interfaces. Regular system testing is crucial to identify and address potential GPIO vulnerabilities before they can be exploited.
| Attack Vector Identification | Hardware Isolation Methods |
|---|---|
| Voltage injection >3.6V | Optocoupler implementation |
| Signal spoofing via UART | Schottky diode protection |
| Side-channel monitoring | LVCC level shifting |
| Power rail manipulation | Removable GPIO headers |
Your GPIO security measures must incorporate voltage regulation techniques beyond encryption. User permission management via udev rules restricts non-root access, but can’t prevent physical tampering. When deploying IoT solutions, remember: encryption protects data transmission, but electrical isolation protects the hardware itself—a critical distinction for mission-critical deployments.
Hardware vs. Software Security: The Critical Gap in IoT Devices
When your Raspberry Pi’s encrypted data is accessed at rest, you’ll find software-only security solutions fundamentally vulnerable to memory scraping attacks that hardware TPMs would otherwise mitigate through physical isolation.
Your device’s unprotected firmware presents an attack surface where malicious actors could potentially extract encryption keys directly from memory without needing to break the cryptographic implementations themselves. Hardware-based security offers dramatically superior protection against these types of manipulation compared to software-only approaches.
Without hardware roots of trust and secure enclaves that enforce physical boundaries, you’re relying exclusively on operating system protections that can be circumvented through physical access techniques like cold boot attacks or flash memory extraction. Implementing a secure boot process would validate firmware integrity during startup, preventing unauthorized code execution.
Data At Rest Vulnerabilities
While IoT device security encompasses numerous attack vectors, data at rest vulnerabilities constitute one of the most critical exposure points in the Raspberry Pi ecosystem. Your deployment’s susceptibility hinges on proper data classification strategies and extensive user awareness protocols when implementing software encryption frameworks. The complexity of security implementations is further complicated by the diverse ecosystems in which IoT devices like Raspberry Pi operate.
Implementing robust software encryption is essential as threat actors primarily target enterprise-connected IoT devices for lateral movement and data exfiltration. Regular firewall rule updates are critical to adapt to the evolving threat landscape targeting IoT deployments. Proper microSD card verification is essential when setting up encryption on your Raspberry Pi to ensure storage media meets both capacity and security requirements.
| Vulnerability Factor | Mitigation Strategy |
|---|---|
| Insecure Defaults | Configure robust password policies |
| Unencrypted Storage | Implement AES-256 encryption |
| Limited Processing | Implement GDPR/HIPAA protocols |
| Economic Exposure | Deploy risk-based security controls |
When malware like Mirai targets your Raspberry Pi deployment, unencrypted data becomes immediately accessible. You’ll need to balance performance requirements against encryption overhead, particularly when addressing hardware limitations. Software-based encryption solutions offer flexibility through customization pathways, though they can’t match the security assurance of dedicated hardware security modules in high-risk deployments.
Physical Access Trumps Software
Physical security considerations often supersede software encryption protections in the Raspberry Pi ecosystem, creating a fundamental vulnerability paradigm that software-only mitigations can’t address.
When adversaries acquire direct hardware access, they can bypass even robust software encryption implementations through component-level manipulation and side-channel attack vectors.
Your software encryption solution exhibits inherent limitations when confronting physical access vulnerabilities. Unlike hardware security modules that offer isolated execution environments and tamper resistance, software-based protections remain susceptible to direct hardware exploitation. Implementing cryptographic operations on chips would significantly enhance the security posture of Raspberry Pi devices in IoT deployments. Root of trust established in silicon provides a more reliable security foundation than software-based approaches alone. Building a controlled environment for testing various attack vectors can help identify vulnerabilities in your IoT implementations before deployment.
Attackers with physical possession can extract encryption keys through voltage glitching, cold boot attacks, or JTAG interfaces—all circumventing your carefully implemented software safeguards. JTAG debugging capabilities enable attackers to analyze processor states in real-time, compromising security measures.
This hardware-software security gap represents a critical consideration for IoT implementations, as Raspberry Pi deployments often exist in physically accessible environments where software encryption alone proves insufficient against sophisticated threat actors targeting embedded systems.
Practical Encryption Strategies for Sensitive IoT Applications
Implementing robust encryption strategies constitutes a cornerstone of secure IoT application development on Raspberry Pi platforms.
You’ll need to deploy TLS-based encryption protocols for all network communications, while implementing 2048-bit RSA or ECC asymmetric encryption for authentication processes.
For sensitive data at rest, leverage host OS encryption utilities alongside TPMs when available.
For IoT deployments with privacy concerns, implement data anonymization techniques before transmission and storage.
Configure your devices with secure boot mechanisms and properly manage X.509 certificates for device authentication.
Utilize lightweight symmetric encryption for efficient processing while maintaining security integrity.
Your implementation should incorporate role-based access control and ACLs to restrict unauthorized access. Regular updates to these encryption protocols are essential as unencrypted data can be easily compromised by sophisticated threat actors.
When developing sensitive applications, CoAP or MQTT over TLS provides the secure communication backbone needed for mission-critical deployments.
The Advanced Encryption Standard (AES) in 128-bit form offers an excellent balance of security and efficiency for resource-constrained Raspberry Pi devices in IoT environments.
For applications requiring enhanced processing power, consider alternatives like the Intel N95 processor which provides superior computational performance while maintaining energy efficiency.
When setting up your security testing environment, establish a controlled environment for safely experimenting with different encryption implementations without risking production systems.
Third-Party Security Enhancements for Raspberry Pi Deployments
Sophisticated third-party security tools dramatically enhance the defensive posture of Raspberry Pi deployments in hostile network environments.
By implementing security automation frameworks, you’ll reduce human error vectors while streamlining vulnerability remediation processes.
Honeypot deployment strategies offer invaluable threat intelligence, capturing attacker methodologies within controlled environments while diverting them from production assets.
Implement Supervisor for script management to guarantee continuous operation of security daemons post-reboot, maintaining your security posture during system fluctuations.
Physical isolation of equipment in locked storage when not in use provides an additional layer of protection against hardware tampering and unauthorized access.
Robust version control via Git enables cryptographic verification of codebase integrity, facilitating rapid incident response through commit-level security auditing.
These third-party tools create a multi-layered security approach that transcends the limitations of standalone encryption.
When implemented alongside network segmentation and secure communication protocols, you’ll establish a hardened security architecture capable of withstanding sophisticated attack vectors targeting IoT infrastructure.
Hardware-based security systems can benefit from battery backup solutions to ensure continuous monitoring during power outages, similar to comprehensive DIY alarm systems.
Installing Snort IDS/IPS on your Raspberry Pi provides real-time network traffic analysis to detect potential security threats before they compromise your IoT system.
Implementing virtual switches on your Raspberry Pi can enhance network security by isolating critical traffic from potential threats while maintaining efficient communication between authorized devices.
Regulatory Compliance Challenges for Raspberry Pi in Production
Steering through the complex regulatory landscape presents significant challenges for Raspberry Pi deployments in production environments, particularly as IoT cybersecurity frameworks evolve rapidly across jurisdictions.
When implementing Raspberry Pi in industrial applications, you’ll need to navigate stringent compliance standards like PSTI and ETSI EN 303 645, which mandate baseline security requirements for connectable products.
Your IoT implementations must adhere to regulatory frameworks across multiple domains—from factory automation to critical infrastructure monitoring. This necessitates extensive security protocols that extend beyond encryption alone.
The Security Requirements for Connectable Products Regulations impact your product design fundamentally, requiring cross-jurisdictional testing protocols. Compliance isn’t optional; it’s imperative for market viability.
Your security architecture must accommodate scalable solutions while maintaining alignment with continually evolving standards in both EU and US markets.
Balancing Security With Performance in Resource-Limited Environments
When deploying encryption solutions on Raspberry Pi devices, you’re inevitably confronted with the intrinsic tension between robust security protocols and computational overhead in constrained environments.
Resource optimization becomes paramount as symmetric encryption (AES) consumes fewer cycles than asymmetric alternatives, presenting critical security trade-offs.
Without a secure enclave, you’ll need to leverage OTP storage for device-specific keys while implementing selective encryption strategies.
Prioritize encryption for sensitive data streams rather than applying extensive protection that might throttle performance.
Consider offloading cryptographic operations where possible and minimizing background processes.
Regular security audits should quantify computational impact of implemented measures, allowing you to fine-tune the security-performance equilibrium.
Remember that well-configured AES-256 can provide substantial protection with acceptable overhead when properly implemented alongside optimized firewall rules and authentication mechanisms.
Installing Nmap Scripting Engine can enhance security monitoring by automating vulnerability detection on your Raspberry Pi-based IoT deployment.
Like Mini PCs for virtualization, Raspberry Pi devices can benefit from dual Ethernet ports to create segmented network zones for improved security isolation.
Frequently Asked Questions
Can Encryption Protect Against Side-Channel Attacks on Raspberry Pi?
Encryption alone can’t shield your Pi from side-channel vulnerabilities. You’ll need specialized countermeasures like noise injection and masking techniques to bolster encryption effectiveness against power analysis and timing attacks.
How Does Encryption Impact Battery Life in Portable Pi Projects?
Encryption imposes significant trade-offs: you’ll experience 20-30% reduced battery runtime due to heightened CPU utilization. Implement battery optimization through headless configurations, strategic cipher selection, and hardware acceleration where possible.
Are There Legal Restrictions on Encryption Strength for Iot Exports?
Like traversing a digital minefield, you’ll face encryption regulations through export controls—specifically EAR/DSGL frameworks mandate notification for symmetric algorithms exceeding 64-bit and asymmetric exceeding 768-bit for cross-border IoT deployments.
Can Machine Learning Detect Encryption Breaches on Raspberry Pi?
You can implement anomaly detection ML on Pi despite resource constraints. Lightweight models monitor encrypted traffic patterns and data integrity violations, though edge-cloud architectures optimize compute-intensive operations for real-time breach detection.
What Encryption Alternatives Exist When Performance Requirements Are Critical?
For performance-critical scenarios, leverage ChaCha20-Poly1305 (symmetric encryption) instead of AES, or implement ECC (asymmetric encryption) with selective encryption techniques. Hardware offloading via HSMs and protocol delegation to edge nodes optimizes cryptographic overhead.
Encryption is Not Enough to Keep Your Raspberry Pi Secure in IoT Applications
Software encryption fortifies your Raspberry Pi’s defenses, but like a castle with reinforced gates yet unguarded windows, it leaves critical attack vectors exposed. You’ll need to implement multi-layered security protocols—combining cryptographic algorithms with hardware-based authentication mechanisms, network segmentation, and rigorous key management infrastructure. The computational overhead-to-security ratio must be optimized to prevent performance degradation within the Pi’s constrained execution environment. Only a thorough security posture guarantees regulatory attestation.

I am a retired software engineer with experience in a multitude of areas including managing AWS and VMWare development environments. I bought a relative a mini-PC a year ago and have become passionate about the technology and its potential to change how we deploy software.

